Microsoft Teams Admin Center Explained: Access, Features, Tips
A secure, efficient Teams setup starts with smart admin choices. Don’t leave powerful features on the table—read this article to get the most from the Microsoft Teams Admin Center.
Microsoft Teams is the engine driving collaboration for millions of organizations worldwide. But behind every smooth Teams experience is a powerful, often unseen dashboard: the Microsoft Teams Admin Center. This web-based control hub gives IT pros full command to configure, secure, and fine-tune their Teams environment.
For IT and security teams, mastering the Admin Center is essential. A single misstep can open the door to security risks, frustrated users, and compliance headaches. But get it right, and you’ll deliver a Teams experience that’s secure, productive, and perfectly tailored to your organization’s needs.
The Admin Center puts everything at your fingertips: user permissions, security policies, team and channel management, meeting settings, app controls, and usage analytics. Recent updates have streamlined the experience, unifying scattered settings into a single, intuitive interface.
This guide will show you how to access the Admin Center, explore its core features, and avoid the most common configuration pitfalls. You’ll discover how to set policies that safeguard your data while supporting productivity, manage external access with confidence, and tap into new AI-powered tools Microsoft is rolling out through 2024 and 2025.
What Is the Microsoft Teams Admin Center?
The Microsoft Teams Admin Center functions as your dedicated web-based interface for controlling every aspect of Microsoft Teams deployment across your organization. This isn’t just another settings page—it’s a comprehensive management platform that gives you centralized authority over your entire Teams ecosystem.
Through this single portal, you can add and remove teams with specific governance controls, manage user roles and permissions at granular levels, and configure policies that govern messaging behavior, meeting functionality, security protocols, and application access. The system also provides robust monitoring capabilities for external user activities and guest interactions, plus detailed analytics and usage reports that reveal how Teams actually gets used in your organization.
Administrative access follows Microsoft’s role-based security model. Only users assigned specific administrative roles can access the center:
- Global Administrators enjoy full control across all organization settings,
- Teams Administrators manage Teams-specific functions,
- Communications Administrators handle calling and meeting features, and
- Device Administrators oversee Teams-certified hardware deployments.
Configuration quality directly correlates with operational success. Organizations that properly configure their Admin Center experience fewer security incidents, reduced help desk volumes, and higher user satisfaction scores. Conversely, rushed or incomplete configurations often result in data governance problems, unauthorized external access, and policy conflicts that undermine both security and productivity.
| Role | Access level | Key permissions | Best use case |
| Global Administrator | Full access | All Teams and M365 settings | Senior IT leadership |
| Teams Administrator | Teams-specific | Teams management, policies, apps | Dedicated Teams admin |
| Teams Communications Administrator | Communications only | Calling, meetings, voice policies | VoIP specialists |
| Teams Device Administrator | Device management | Hardware, room systems, phones | Device deployment teams |
| Teams Communications Support Engineer | Troubleshooting | Call quality, user support tools | Help desk escalation |
Integration with Microsoft 365
The Teams Admin Center operates as part of Microsoft’s broader administrative ecosystem, connecting directly with other management portals including:
- the Microsoft 365 Admin Center at admin.microsoft.com,
- Exchange Admin Center for email and calendar integration,
- SharePoint Admin Center for document storage and collaboration settings, and
- the Security & Compliance Center for policy enforcement.
This integration creates both opportunities and requirements for administrators. Most user management tasks—adding accounts, assigning licenses, setting global policies—happen in the Microsoft 365 Admin Center. The Teams Admin Center then provides specialized controls for Teams-specific settings like messaging policies, meeting configurations, and application permissions.
💡 Consider a practical example: when you add a new employee, you’ll create their account and assign licenses through the Microsoft 365 Admin Center. But determining whether they can use chat features, join external meetings, or install third-party applications requires configuration in the Teams Admin Center. This division of responsibilities allows for both comprehensive control and specialized management of Teams-specific features.
The bundled approach delivers end-to-end control over Teams workflows while maintaining consistency across your Microsoft 365 environment. Changes made in one admin center often affect settings visible in others, creating a unified but complex management experience that requires understanding multiple interfaces.
Interface and navigation
The Teams Admin Center presents a modern web interface built around a left navigation panel that organizes management functions into logical sections. The dashboard provides quick access to key metrics and recent activities, while individual sections contain detailed configuration options and management tools.
Key interface sections include
- Teams for managing team creation, deletion, properties, and member assignments;
- Users for viewing user lists, managing individual policies, and configuring calling settings;
- Devices for controlling registered Teams hardware like conference systems and desk phones;
- Locations for setting up office addresses, phone numbers, and regional parameters; and
- Voice for managing telephony features in organizations using Teams as their phone system.
The Policies section serves as the control center for behavior management, containing settings for messaging permissions, meeting configurations, application access, call recording policies, and more.
Analytics & Reports provides usage metrics, user activity data, and connection quality information.
Teams Apps manages application installation, permissions, and availability across your organization.
Org-wide settings controls global features like external access, guest permissions, and Teams templates.
Interface elements adapt based on your administrative permissions. Users with limited roles see only relevant sections, while Global Administrators access the complete feature set. This role-based interface design prevents accidental changes to areas outside your administrative scope while maintaining a clean, focused user experience for your specific responsibilities.

👉What is the admin site for Teams? The admin site for Teams is the Microsoft Teams Admin Center, accessible at https://admin.teams.microsoft.com. This web-based portal serves as the centralized management interface for all Teams-related administrative functions. It integrates with the broader Microsoft 365 admin ecosystem while providing Teams-specific controls and configurations.
How to Access Teams Admin Center
Getting into the Teams Admin Center requires the right credentials and permissions. The process itself is straightforward, but understanding the access requirements and available entry points will save you time and prevent common login issues.
Where is Teams Admin Center?: How to get to Teams Admin Centre
The Teams Admin Center operates from a single, dedicated URL: https://admin.teams.microsoft.com. This web-based portal requires no software installation or downloads—just internet access and a corporate Microsoft 365 account with appropriate administrative permissions.
The portal functions reliably across modern browsers including Edge, Chrome, and Firefox. Microsoft optimizes the interface primarily for Edge, but cross-browser compatibility remains strong for daily administrative tasks. You’ll find the most consistent experience using Chromium-based browsers, though Firefox handles most functions without issues.
How do I get to the Microsoft Teams Admin Center?: How to log in
Accessing the Admin Center follows a straightforward process:
- Navigate to https://admin.teams.microsoft.com and sign in using your corporate Microsoft 365 credentials.
- The system will verify your administrative permissions before granting access to the interface.
Required roles for access include:
- Global Administrator, which provides complete access to all organization settings and Teams management functions;
- Teams Administrator, which offers comprehensive Teams-specific management capabilities;
- Teams Communications Administrator, focused on calling and meeting feature management;
- Teams Communications Support Engineer and Specialist, which provide varying levels of troubleshooting access;
- Teams Device Administrator for managing Teams-certified hardware; and
- the newer Teams Telephony Administrator role for telephony-specific functions.
Users without proper administrative roles receive access denied errors when attempting to log in. The system displays specific error messages indicating insufficient permissions rather than generic login failures.
Alternative access paths exist through the broader Microsoft 365 ecosystem. From https://admin.microsoft.com, locate “Teams Admin” in the left navigation panel or use the search function to find Teams administration options. This method provides the same access levels but requires an additional navigation step.
👉 What is Teams admin console? The Teams admin console, officially called the Microsoft Teams Admin Center, is a web-based management portal located at admin.teams.microsoft.com that provides comprehensive control over your organization’s Teams environment. It allows administrators to manage users, teams, policies, applications, and security settings from a centralized interface. Only users with specific administrative roles like Global Administrator or Teams Administrator can access this console to configure and monitor Teams deployments.
How to find out who is an administrator
Identifying current administrators requires access to the Microsoft 365 Admin Center at https://admin.microsoft.com.
- Navigate to “Users” then “Active users” to view your organization’s user list.
- Opening individual user profiles reveals assigned administrative roles under the roles section.
For comprehensive administrator visibility, use the role-based filtering options within the Active users section or navigate directly to “Roles” then “Role assignments.” This approach displays all users organized by their administrative responsibilities, making it easier to audit current permissions and identify potential access issues.
Regular administrator auditing serves multiple purposes:
- Ensuring proper role assignments match current job responsibilities,
- Identifying unused administrative accounts that pose security risks, and
- Maintaining compliance with organizational access policies.
Many organizations schedule quarterly reviews of administrative permissions to maintain security hygiene and prevent privilege creep over time.
The audit process also helps identify training needs. Administrators assigned roles without proper Teams management experience may require additional education to avoid configuration mistakes that impact organizational productivity and security posture.
👉 What does the Teams Admin Center look like? The Teams Admin Center features a modern web interface with a left navigation panel organizing functions into logical sections like Teams, Users, Devices, Policies, and Analytics. The main dashboard displays key metrics and recent activities, while individual sections contain detailed configuration options presented through cards, tabs, and settings pages. The interface adapts to show only relevant sections based on your administrative permissions.
Key Features of the Teams Admin Center
The Teams Admin Center organizes its capabilities into distinct functional areas, each designed to address specific administrative needs. Understanding these core features helps you prioritize configuration tasks and maintain control over your Teams environment.
Managing teams and users
The Teams Admin Center provides comprehensive control over your organization’s team structure and user permissions. You can manually create teams with predefined templates, delete obsolete or unused teams to maintain organizational hygiene, and assign owners who possess the authority to manage team-specific settings, invite members, and control channel creation.
Team management extends beyond basic creation and deletion. The interface displays detailed information about each team including the number of standard, private, and shared channels, current member counts, assigned owners, and guest user statistics. This visibility helps administrators identify teams that may need attention due to inactivity, excessive growth, or unusual guest access patterns.
User management capabilities include viewing comprehensive user lists with Teams-specific information, controlling team membership and access permissions, managing license assignments and account status, and troubleshooting user-specific issues through call quality data and device information. The system also provides tools for bulk operations, allowing efficient management of large user populations.
Recent updates have significantly enhanced user management capabilities. Microsoft introduced unified settings and policies management in mid-2024, consolidating previously scattered configuration options into a single “Settings & policies” tab. This change eliminates the need to navigate multiple locations for different Teams configurations, reducing administrative overhead and potential configuration errors.
Role-based administration remains crucial for effective delegation. As mentioned, the Admin Center supports built-in roles including Teams Administrator for comprehensive Teams management, Communications Administrator for calling and meeting oversight, and Device Administrator for hardware management. These roles allow organizations to distribute administrative responsibilities without granting excessive permissions to individual users.
Setting up policies
Policy configuration represents the most powerful aspect of Teams administration. These rules determine how Teams behaves for different users or groups, creating consistent experiences while maintaining security and compliance requirements.
Messaging policies control fundamental chat and channel communication features. Administrators can configure permissions for message editing and deletion, Giphy usage and content ratings, sticker and meme permissions, read receipt visibility, and priority message capabilities. These controls prove essential for organizations with specific communication standards or regulatory requirements.
Meeting policies define the video conferencing experience across your organization. Settings include audio and video permissions, screen sharing capabilities, meeting recording options, transcription services, and breakout room functionality. The granular control allows different policies for executive teams, general employees, and external meeting participants.
App setup policies determine which applications appear in users’ Teams interfaces by default. Organizations can create department-specific policies that pin relevant applications—GitHub and DevOps tools for developers, Planner and campaign calendars for marketing teams, or survey applications for HR departments while blocking potentially problematic third-party integrations.
Voice policies become critical for organizations using Teams Phone capabilities. These settings control call forwarding, voicemail access, emergency calling configurations, and integration with existing telephony systems. Proper voice policy configuration ensures compliance with local regulations while maintaining call quality and reliability.
| Policy type | Controls | User impact | Configuration complexity |
| Messaging | Chat features, GIFs, editing | Daily communication | Low |
| Meeting | Video, recording, sharing | Meeting experience | Medium |
| App Setup | Available apps, pinned apps | Productivity tools | Medium |
| Voice/Calling | Phone features, forwarding | Communication methods | High |
| External Access | Guest permissions, domains | Collaboration scope | High |
Enhanced Copilot controls represent a major 2024 addition to policy management. Administrators now possess granular control over how users access and utilize Microsoft’s AI assistant during and after meetings. These policies address growing organizational concerns about AI data processing while enabling productivity benefits where appropriate.
Security and privacy
Security configuration through the Teams Admin Center addresses multiple threat vectors and compliance requirements. Access level controls define administrative permissions and user capabilities within teams, channels, and applications. These settings create hierarchical permission structures that match organizational roles and responsibilities.
Guest access management provides detailed control over external user permissions. Administrators can restrict guest access to specific chat features, file sharing capabilities, and application usage. The system supports time-limited guest access, automatic guest removal, and detailed audit logging of guest activities.
👉 Learn more about guest access management in our dedicated articles:
- Maximizing Collaboration: Microsoft Teams Guest Access Guide
- Microsoft Teams External Users: Collaboration Guide, Tips & Limitations
External access controls govern interactions with users from other Microsoft 365 organizations. Settings include domain-specific allow and block lists, federation controls for Skype for Business integration, and cross-tenant collaboration restrictions. Recent updates include enhanced external access analytics that provide insights into cross-organizational collaboration patterns.
Information protection integration connects Teams with Microsoft’s broader security ecosystem. The Admin Center supports Data Loss Prevention (DLP) policies, sensitivity labels for automatic content classification, and integration with Microsoft Defender for Office 365. These connections ensure consistent security policy enforcement across all Microsoft 365 applications.

New security features include meeting chat restrictions that prevent copying or forwarding of meeting conversations, bot blocking policies with CAPTCHA verification for anonymous users, and enhanced screen capture protection that turns meeting windows black when capture attempts are detected. These features address evolving security threats in hybrid work environments.
The Admin Center also provides integration points with Conditional Access policies, allowing administrators to enforce device compliance, location restrictions, and multi-factor authentication requirements specifically for Teams access. This integration ensures Teams security aligns with broader organizational security policies.
Manage Apps with the Admin Center
Application management represents one of the most critical aspects of Teams administration. The wrong apps can create security vulnerabilities, compliance issues, and productivity problems. The right apps, properly configured, enhance collaboration and streamline workflows across your organization.
Find and install apps
The Teams Admin Center grants administrators complete authority over application availability and deployment across your organization. Through the Teams apps → Manage apps section, you can browse applications from the Microsoft Teams App Store, initiate installations for specific teams or individual users, and control access to third-party applications, custom solutions, and built-in Microsoft integrations.
App Permission Policies serve as the primary mechanism for controlling application access and behavior. These policies determine which applications specific user groups can access, install, or interact with during their Teams sessions. You can create restrictive policies that allow only trusted or internal applications while blocking everything else, or implement selective policies that permit only Microsoft 365 native apps like Calendar, Planner, and Forms.
Department-specific policies prove particularly valuable for maintaining security while enabling productivity. HR departments might receive access to survey and feedback applications while being restricted from development tools. Conversely, engineering teams could access GitHub integrations and DevOps applications while being blocked from external communication bots that might pose security risks.
The installation process supports both administrator-initiated deployments and user-requested installations subject to policy approval. Administrators can push critical applications to entire departments or specific teams, ensuring consistent tooling across user groups. User-initiated requests flow through approval workflows that maintain administrative oversight while reducing deployment bottlenecks.
Managing app access
Application data access represents a critical security consideration that requires careful administrative oversight. Many Teams applications request permissions to access user data including messages, files, calendar events, and contact information. The Admin Center provides detailed permission review capabilities that allow administrators to assess risk levels and approve or deny access at organizational or group levels.
App Setup Policies offer granular control over the user interface experience. These policies determine which applications appear pinned to the left navigation panel by default, creating customized experiences that match departmental needs and workflows. Marketing teams might see campaign management tools and social media integrations prominently displayed, while finance departments could have expense tracking and reporting applications readily accessible.
The policy system supports inheritance and override capabilities, allowing broad organizational defaults with specific exceptions for particular user groups. This flexibility enables consistent baseline configurations while accommodating unique departmental requirements without compromising security standards.
Data access controls extend beyond simple allow/deny decisions. Administrators can configure conditional access that requires additional authentication for sensitive applications, restrict data sharing capabilities for external applications, and implement time-based access controls that automatically revoke permissions after specified periods.
👉 How to see who is Teams admin? Go to the Microsoft 365 Admin Center at admin.microsoft.com, navigate to “Users” then “Active users,” and open individual user profiles to view their assigned administrative roles. For a comprehensive view, go to “Roles” then “Role assignments” to see all users organized by their administrative responsibilities including Teams Administrator, Global Administrator, and other Teams-related roles. You can also use role-based filtering to quickly identify users with specific administrative permissions.
Monitoring and analytics
Application usage analytics provide essential insights for optimizing your Teams app ecosystem. The Admin Center generates comprehensive usage reports that reveal which applications see the highest adoption rates, identify teams or departments with low engagement, and track installation patterns across your organization.
App Adoption Trends help administrators understand how effectively deployed applications serve their intended purposes. These metrics prove valuable when deciding whether to renew third-party application licenses, remove underutilized applications, or provide additional training to boost adoption rates.
Export capabilities allow detailed analysis through Excel or other business intelligence tools. Administrators can segment usage data by department, team size, or application category to identify trends and optimization opportunities. This data proves particularly useful during budget planning cycles when evaluating the return on investment for various application subscriptions.
The analytics also reveal security-relevant patterns such as unusual installation requests, applications generating high volumes of data access requests, or user attempts to install blocked applications. These insights help administrators refine policies and identify potential security training needs across different user populations.
Recent enhancements to app management include improved integration with Microsoft’s broader security ecosystem, providing enhanced visibility into app permissions and data access patterns. These updates help administrators maintain better oversight of their application ecosystems while supporting productive user experiences.
Advanced Management of Microsoft Teams
Microsoft Teams administration extends far beyond basic user and app management. Advanced features enable enterprise-scale deployment, integration with broader Microsoft 365 services, and sophisticated device management that supports modern hybrid work environments.
Working with devices and locations
The Microsoft Teams Admin Center includes a dedicated Devices section that displays and manages all registered Teams-certified hardware across your organization. This encompasses Teams Rooms systems for conference spaces, IP phones and desk devices, conference room displays and touch panels, and compatible headsets and peripherals that support Teams functionality.
Device management capabilities extend beyond simple inventory tracking. Administrators can remotely update firmware across entire device fleets, monitor real-time device status including connectivity and performance metrics, configure device-specific policies such as automatic screen timeouts and security settings, and assign devices to specific physical locations for organized management.
The Locations feature enables sophisticated organizational mapping that supports distributed Teams deployments. You can organize device management by physical offices, regions, or buildings, assign location-specific policies and configurations, and use geographic data to analyze Teams infrastructure performance across different sites.
This location-based approach proves especially valuable for global organizations managing complex hybrid work environments. Branch offices can maintain standardized hardware configurations while adapting to local regulatory requirements or network conditions. Regional administrators can manage location-specific devices without affecting other geographical deployments.
Recent updates have introduced streamlined Role-Based Access Controls (RBAC) for device management, creating unified permissions across the Teams Admin Center and Teams Rooms Pro Management portals. This integration eliminates permission inconsistencies that previously complicated device administration across different interfaces.
Additionally, Microsoft has introduced an AI assistant in the Pro Management portal to help administrators quickly find answers about Teams meeting spaces and receive data-driven insights specific to their organization’s device inventory. This assistant reduces troubleshooting time and provides proactive maintenance recommendations.
👉 To stay on top of updates & developments for Teams, check out the Release notes for Microsoft Teams admin features on a regular basis.
Integration with other M365 services
Teams operates as part of the broader Microsoft 365 ecosystem, creating both opportunities and administrative requirements across multiple service boundaries. The Team Admin Center coordinates with other administrative interfaces to maintain consistent policies and user experiences.
SharePoint Online integration handles all file storage and sharing within Teams. Every team creates an associated SharePoint site that stores shared documents, channel files, and collaborative content. The Admin Centers allow coordinated control over document access permissions, storage quotas and retention policies, and backup and recovery procedures. Administrators must understand SharePoint’s permission inheritance model to properly secure Teams file sharing.
OneDrive for Business manages personal file storage and private chat document sharing. Users’ OneDrive accounts store files shared in private conversations and personal document libraries. The Microsoft 365 Admin Center provides controls for OneDrive retention policies, external sharing restrictions, and data recovery procedures that directly affect Teams functionality.
👉 Learn more about OneDrive in dedicated articles on our blog:
- What Is Microsoft OneDrive for Business and How to Use It Effectively?
- OneDrive vs SharePoint: Key Differences Explained
Exchange Online powers Teams calendar integration, meeting scheduling, and notification systems. Teams meetings automatically sync with Outlook calendars, and meeting invitations flow through Exchange infrastructure. The Exchange Admin Center manages email retention policies, calendar synchronization settings, and meeting room resource booking that impacts Teams meeting experiences.
These service interdependencies require coordinated administration across multiple interfaces. Changes in SharePoint permissions affect Teams file access. Exchange policies impact meeting functionality. OneDrive restrictions influence private chat capabilities. Successful Teams administration requires understanding these connections and maintaining consistent policies across all integrated services.
The integration extends to security and compliance systems as well. Microsoft Defender for Office 365 protects Teams against malware and phishing attacks. Compliance Center policies govern data retention and legal hold requirements. Azure Active Directory controls authentication and conditional access policies that affect Teams login and device access.
Common Errors and Issues
Despite the comprehensive capabilities available through the Microsoft Teams Admin Center, many organizations encounter preventable configuration mistakes that create security vulnerabilities, compliance problems, and user frustration. Understanding these common pitfalls helps administrators build more secure and manageable Teams environments.
| Error | Symptoms | Root cause | Quick fix |
| Guest access proliferation | Unauthorized external users | No approval workflow | Enable guest approval policies |
| App installation chaos | Unapproved apps everywhere | Default allow-all policy | Implement app permission policies |
| Policy conflicts | Inconsistent user experience | Overlapping configurations | Audit and consolidate policies |
| Missing team owners | Unmanaged teams | No ownership governance | Assign 2-3 owners per team |
| External domain access | Security vulnerabilities | Open external access | Configure domain allow/block lists |
Assigning all users as owners
Organizations frequently make the mistake of assigning all users as team owners by default when creating teams. This approach seems efficient during initial deployment but creates significant governance and security problems over time.
Team owners possess extensive permissions including the ability to delete entire teams, modify team settings and policies, invite external members without oversight, change channel configurations, and alter team membership. When everyone has owner permissions, organizations lose meaningful control over their Teams environment and struggle to maintain visibility into important changes.
The problem compounds as teams grow and evolve. Multiple owners often make conflicting changes, creating confusion about team purpose and access controls. Security incidents become harder to trace when numerous users can modify critical settings. Compliance audits become more complex when ownership responsibilities aren’t clearly defined.
Best practices recommend limiting ownership to 2-3 individuals per team who have clear responsibilities for team governance. Train designated owners on their administrative duties and the security implications of their permissions. Configure automatic notifications for ownership changes to maintain visibility into team management activities. Consider implementing approval workflows for owner assignments in sensitive teams or departments.
No control over guests
Guest access remains enabled by default in many Teams deployments, but organizations often fail to implement appropriate control measures. This oversight creates significant data security risks and compliance challenges that may not become apparent until external access incidents occur.
Uncontrolled guest access allows external users to access confidential information through shared channels and files. Organizations lose visibility into who can access sensitive data and struggle to maintain audit trails for external collaborations. Compliance frameworks often require specific controls over external data access that default guest settings don’t provide.
The risks extend beyond data exposure. Guest users might inadvertently or intentionally invite additional external participants, creating access chains that exceed organizational security policies. Inactive guest accounts accumulate over time, creating unnecessary attack vectors and compliance audit findings.
Implement guest approval policies that require administrative review before external access grants. Use Azure AD Access Reviews (now part of Microsoft Entra ID Governance) to conduct regular audits of guest user accounts and remove inactive or unnecessary access. Configure guest activity restrictions that prevent external users from creating channels, editing shared files, or accessing sensitive applications. Establish clear guest access policies that define appropriate use cases and approval processes.
👉 Read more about MS Teams governance in our dedicated piece: Microsoft Teams Governance for Enhanced Collaboration and Security
Ignoring application access policies
Many administrators allow installation of all available applications without implementing appropriate access restrictions. This approach creates significant security risks when users install applications that request broad permissions to access organizational data including files, chat histories, and calendar information.
Unrestricted app access enables data exfiltration through third-party applications that may have inadequate security controls or unclear data handling practices. Organizations lose control over where sensitive information gets processed and stored. Compliance requirements often mandate specific controls over third-party data access that default settings don’t provide.
The problem becomes more complex as users install applications independently without understanding permission implications. Applications might request access to entire organizational directories, email systems, or file repositories. Some applications continue processing organizational data even after users stop actively using them.
Configure App Permission Policies that implement allow-list approaches for application installations. Regularly audit installed applications through usage analytics reports to identify unnecessary or risky applications. Implement approval workflows for new application requests that include security and privacy assessments. Train users to understand application permission requests and report potentially problematic applications to IT departments.
Misunderstanding role division between admin centers
Administrators often struggle with understanding which administrative functions belong in the Microsoft 365 Admin Center versus the Teams Admin Center. This confusion leads to incomplete configurations, policy conflicts, and inefficient administrative workflows.
The Microsoft 365 Admin Center handles user account creation, license assignments, and global policy settings that affect all Microsoft 365 services. The Teams Admin Center manages Teams-specific policies, team creation and management, and application permissions that only apply within Teams. Attempting to perform user management tasks in the wrong interface creates confusion and incomplete configurations.
Common examples include trying to assign Teams licenses through the Team Admin Center, attempting to create user accounts from Teams management interfaces, or looking for global security policies in Teams-specific settings. These interface misunderstandings waste administrative time and can result in users having incomplete access to required functionality.
Review Microsoft’s official role and responsibility documentation to understand the proper division of administrative tasks. Create internal responsibility matrices when multiple administrators manage different aspects of your Microsoft 365 environment. Establish clear procedures that specify which interface to use for different types of configuration changes.
💡 Learn more about roles and responsibilities across Microsoft products and services through Microsoft Learn, a free online learning platform that helps individuals develop technical skills and knowledge for Microsoft technologies.
Insufficient attention to security with external integrations
Teams administrators often approve third-party applications and external integrations without adequate security assessment of their data handling practices and permission requirements. This oversight can result in unauthorized data access, compliance violations, and integration of poorly secured external systems.
External integrations might request access to organizational data that exceeds their functional requirements. Some applications store data in geographic regions that violate data residency requirements. Others may have inadequate security controls that expose organizational information to external threats or unauthorized access.
The risks extend beyond individual applications to include connected services and data processing chains. An approved application might share data with additional third-party services that weren’t part of the original assessment. Updates to external applications can change their data handling practices without organizational awareness.
Implement systematic security assessments for all external integrations that include data flow analysis, geographic processing location verification, and ongoing monitoring requirements. Use Microsoft Cloud App Security or Microsoft Defender for Cloud Apps to maintain visibility into external data connections. Establish regular reviews of approved integrations to ensure they continue meeting security and compliance requirements.
No regular auditing and monitoring
Many organizations configure their Teams environment during initial deployment but fail to implement ongoing monitoring and audit procedures. This oversight allows configuration drift, unauthorized changes, and security issues to accumulate without detection.
Without regular auditing, administrators lose visibility into policy changes, user permission modifications, and application installations that might affect security or compliance postures. Inactive teams and user accounts accumulate over time, creating unnecessary attack surfaces and audit findings. Guest access permissions may expire or become inappropriate without regular review.
Configuration changes often happen incrementally through multiple administrators or automated processes. Without systematic monitoring, organizations struggle to maintain consistent security policies and may discover compliance issues only during formal audits or security incidents.
Implement regular review schedules for team compositions, owner assignments, and guest access permissions. Use Teams usage reports and audit logs to identify unusual activity patterns or policy violations. Configure automated alerts for critical configuration changes such as new external domains, application installations, or policy modifications. Establish quarterly reviews of overall Teams configuration to ensure alignment with organizational security and compliance requirements.
Neglecting user training and team owner education
Organizations often grant Teams access and administrative permissions without providing adequate training on proper usage, security considerations, and administrative responsibilities. This oversight leads to policy violations, security incidents, and ineffective team management across the organization.
Untrained team owners may inadvertently create security risks by inviting inappropriate external guests, misconfiguring channel permissions, or installing problematic applications. Users without proper security awareness training might fall victim to phishing attacks or social engineering attempts targeting Teams functionality.
The complexity of Teams features and integration with other Microsoft 365 services requires users to understand both functional capabilities and security implications of their actions. Without proper training, users make decisions that compromise organizational security or violate compliance policies without understanding the consequences.
Develop comprehensive training programs for team owners that cover security responsibilities, proper guest management, and policy compliance requirements. Provide security awareness training that specifically addresses Teams-related threats such as malicious applications, external collaboration risks, and social engineering attacks. Create internal documentation and quick reference guides that help users make appropriate decisions about Teams usage and external collaboration.
Recommendations for Administrators
Effective Teams administration requires proactive management, regular maintenance, and continuous attention to security and compliance requirements. The following recommendations help administrators maintain secure, productive Teams environments while avoiding common configuration problems.
Practical tips
Effective Teams administration requires consistent habits and proactive maintenance. The following recommendations help administrators maintain secure, productive Teams environments while preventing common configuration problems before they impact users.
Review team and user settings monthly
Monthly audits of your Teams environment prevent configuration drift and identify potential security issues before they become significant problems. Review team composition to ensure all teams have appropriate owners and that inactive teams get archived or deleted. Examine user activity patterns to identify accounts that may need attention due to unusual behavior or extended inactivity.
Owner role assignments deserve particular attention during these reviews. Teams with too many owners create governance problems, while teams without active owners risk becoming unmanaged. Verify that all teams maintain current owners who understand their responsibilities and actively manage their team’s security and compliance posture.
Policy compliance requires ongoing verification as organizational needs evolve. Teams that were appropriate when created may no longer align with current security requirements or business objectives. Regular reviews help identify teams that need policy updates, additional security controls, or administrative attention.
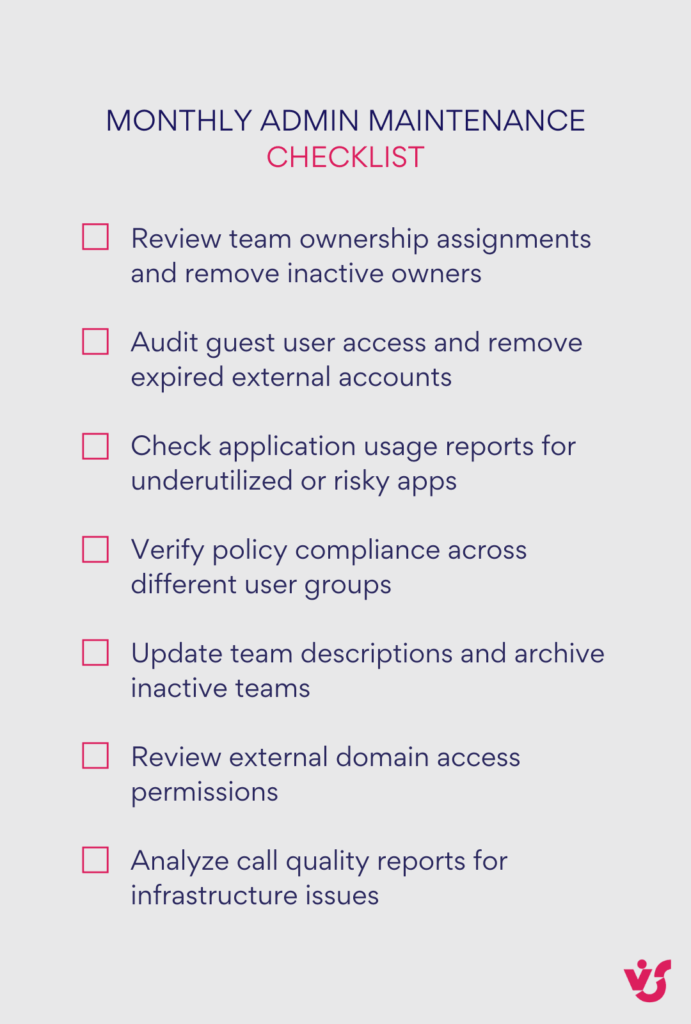
Use policy packages for standardized deployments
The MS Teams Admin Center provides pre-configured policy packages designed for specific organizational roles including education environments with teacher and student policies, frontline workers with shift management and communication policies, and healthcare settings with HIPAA-compliant configurations. These packages deliver tested combinations of messaging, meeting, app, and calling policies that work together effectively.
Policy packages significantly reduce configuration time while ensuring consistent security and functionality across similar user groups. Rather than manually configuring individual policies for each department, you can deploy appropriate packages and customize them for specific organizational requirements.
Custom policy packages prove valuable for organizations with unique requirements that don’t match standard templates. You can create department-specific packages that combine messaging policies for internal communications, meeting policies for client interactions, and app policies for required productivity tools. These custom packages ensure consistent deployments while accommodating specific business needs.
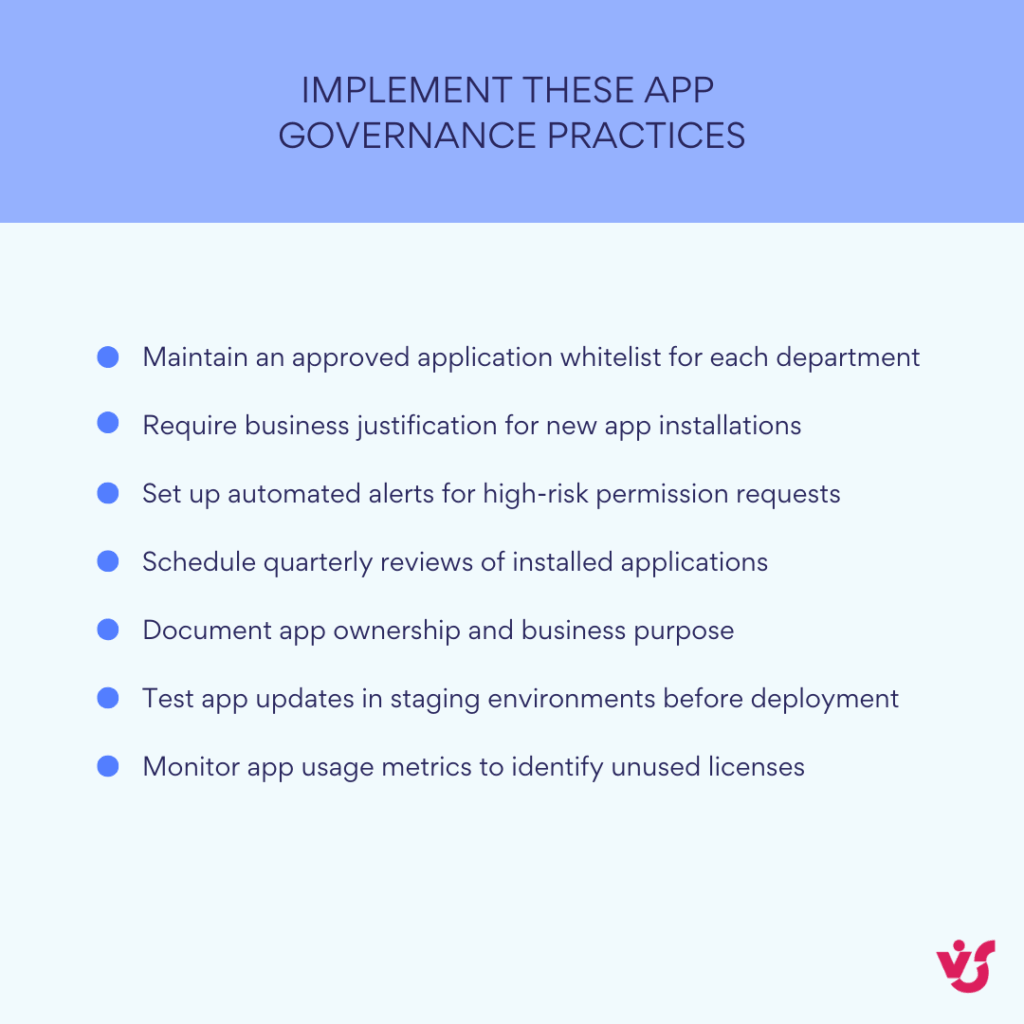
Restrict unauthorized application installations proactively
App Permission Policies should implement allow-list approaches rather than reactive blocking of problematic applications. Configure policies that permit only verified applications from trusted publishers, restrict installation of applications requiring extensive data permissions, and require administrative approval for applications with external data processing requirements.
User group segmentation enables appropriate application access without compromising security. Development teams might need access to GitHub and development tool integrations, while finance departments require expense management and reporting applications. Marketing teams could access social media management tools that would be inappropriate for other departments.
Regular application audits help identify installations that may have bypassed policy controls or become inappropriate over time. Export application usage reports to identify rarely used applications that consume licenses unnecessarily, applications requesting excessive permissions relative to their usage, and applications with unusual data access patterns that might indicate security concerns.
Implement comprehensive user training programs
Team owner training should cover security responsibilities, proper guest management procedures, policy compliance requirements, and escalation procedures for security concerns. Owners need to understand the security implications of their decisions and know how to respond to potential security incidents within their teams.
General user security awareness training must address Teams-specific threats including malicious application installations, social engineering attacks through Teams messaging, and proper handling of sensitive information in shared channels. Users should understand how to identify and report suspicious activity, recognize legitimate versus potentially harmful external collaboration requests, and follow organizational policies for data sharing and external communications.
Documentation and quick reference guides help users make appropriate decisions without requiring extensive training sessions. Create simple checklists for common tasks like inviting external guests, installing applications, and sharing sensitive documents. Provide clear guidance on when to contact IT support and how to report potential security incidents.
Establish monitoring and alerting systems
Automated monitoring reduces the administrative burden of tracking configuration changes while ensuring rapid response to potential security issues. Configure alerts for critical events including new external domain additions, high-privilege role assignments, and policy modifications that affect security or compliance postures.
Usage reports should be reviewed regularly to identify trends that might indicate security concerns or training needs. Unusual application installation patterns, excessive guest access requests, or teams with abnormal growth rates may require administrative attention. Export and analyze usage data to identify optimization opportunities and potential security risks.
Audit log retention ensures compliance with organizational record-keeping requirements while providing necessary data for security incident investigations. Configure appropriate retention periods for different types of audit data and establish procedures for accessing historical information when security incidents occur.
Maintain detailed documentation of configuration changes
Configuration change logs provide essential information for troubleshooting problems, rolling back problematic changes, and maintaining compliance with organizational change management requirements. Document who made changes, when they occurred, what specific settings were modified, and the business justification for each change.
This documentation proves invaluable during security incidents when administrators need to understand recent changes that might have contributed to problems. It also helps during staff transitions when new administrators need to understand the reasoning behind current configurations.
Version control for policy configurations enables rapid rollback of problematic changes and helps administrators understand the evolution of their Teams environment over time. Many organizations maintain configuration templates that can be quickly deployed to restore known-good states when problems occur.
Where to look for help
No administrator masters Teams management in isolation. Microsoft provides comprehensive documentation, while community resources and professional networks offer practical insights from experienced practitioners facing similar challenges.
Official Microsoft documentation
Microsoft maintains comprehensive, continuously updated documentation for Teams administration at https://learn.microsoft.com/en-us/microsoftteams/. This resource provides step-by-step configuration instructions, detailed explanations of policy settings and interactions, and API documentation for organizations implementing automated management solutions.
The Microsoft 365 Admin Center documentation at https://admin.microsoft.com includes essential information about user management, license assignment, and global policy configuration that affects Teams functionality. Understanding both resources ensures comprehensive knowledge of the integrated administrative environment.
Community resources and professional networks
The Microsoft Tech Community at https://techcommunity.microsoft.com/category/MicrosoftTeams provides access to Microsoft specialists and experienced administrators who share solutions to common problems and discuss best practices for complex deployments. The community forums offer practical insights that complement official documentation.
Microsoft Support provides direct assistance for organizations with corporate subscriptions. Access support through the Microsoft 365 portal or through Microsoft partner networks. Corporate support includes access to escalation procedures for critical issues and guidance on complex configuration scenarios.
💡 Learn more about getting support from Microsoft: Get support for Microsoft 365 for business
Developer and automation resources
GitHub repositories and the Microsoft Teams Developer Blog offer valuable resources for administrators implementing PowerShell automation, Graph API integrations, and custom solutions for Teams management. These resources prove particularly valuable for large organizations requiring automated provisioning and management capabilities.
The Microsoft 365 YouTube Channel publishes regular video tutorials, feature demonstrations, and walkthroughs of typical use cases for Teams and related administrative tools. Video content often provides clearer explanations of complex configuration procedures than written documentation alone.
Third-party tools and integrations
Organizations seeking enhanced Teams functionality can explore third-party solutions that integrate with Microsoft Teams while maintaining security and compliance standards. Solutions like VirtoSoftware’s Teams applications provide additional capabilities for polling, project management, calendar coordination, and notification systems that extend Teams functionality without compromising administrative control.
These third-party tools often provide features that address specific organizational needs not covered by standard Teams functionality, such as advanced polling capabilities, specialized project management workflows, or enhanced calendar integration that supports complex scheduling requirements.
Additional tools—VirtoSoftware apps for Teams
Administrators seeking to enhance their Teams environment beyond standard functionality can consider VirtoSoftware’s suite of productivity applications. These tools integrate directly with Microsoft Teams while maintaining enterprise-grade security standards and administrative controls.
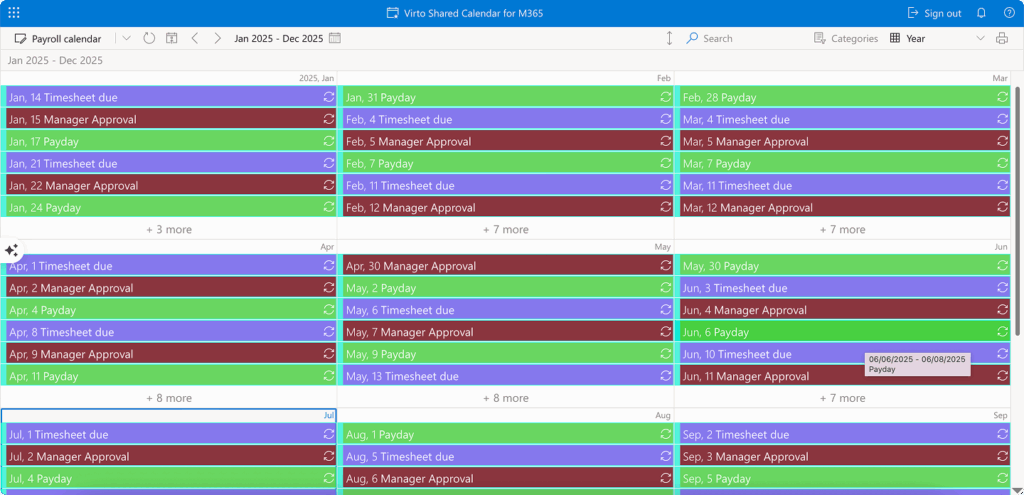
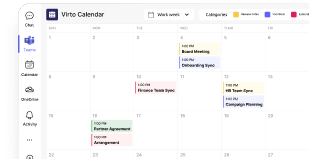
Virto Shared Calendar for Teams provides enhanced calendar functionality that goes beyond Teams’ native scheduling capabilities. This application enables simple event creation and management with color-coded tagging, anonymous access for external collaborators, and cross-platform availability as both a Teams app and standalone web application. The tool proves particularly valuable for organizations requiring external calendar sharing without Microsoft account requirements.
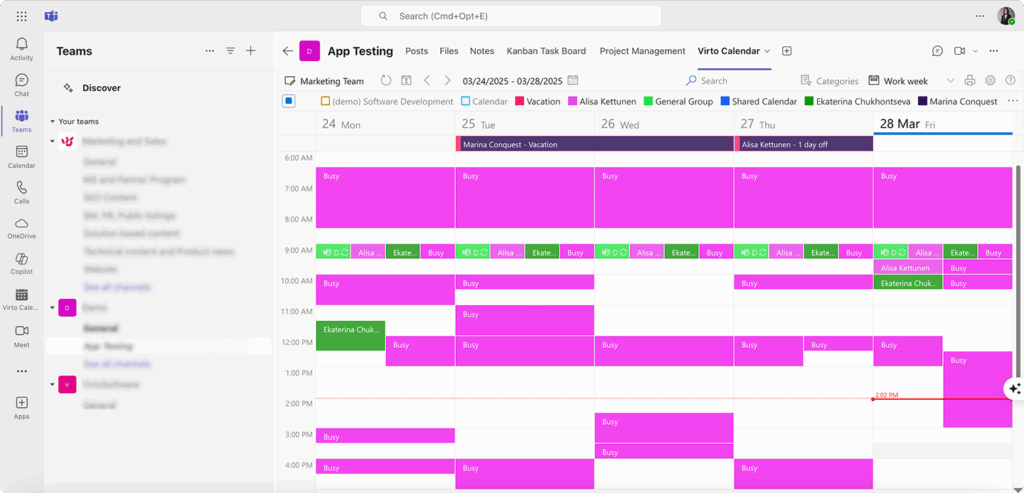
Virto Calendar App for Teams offers comprehensive calendar overlay functionality that consolidates events from multiple sources including SharePoint, Exchange, Google, and iCalendar feeds. This integration provides administrators with unified calendar management while supporting diverse calendar ecosystems within their organizations. The application includes various view options and categorization features that enhance schedule visibility across teams.
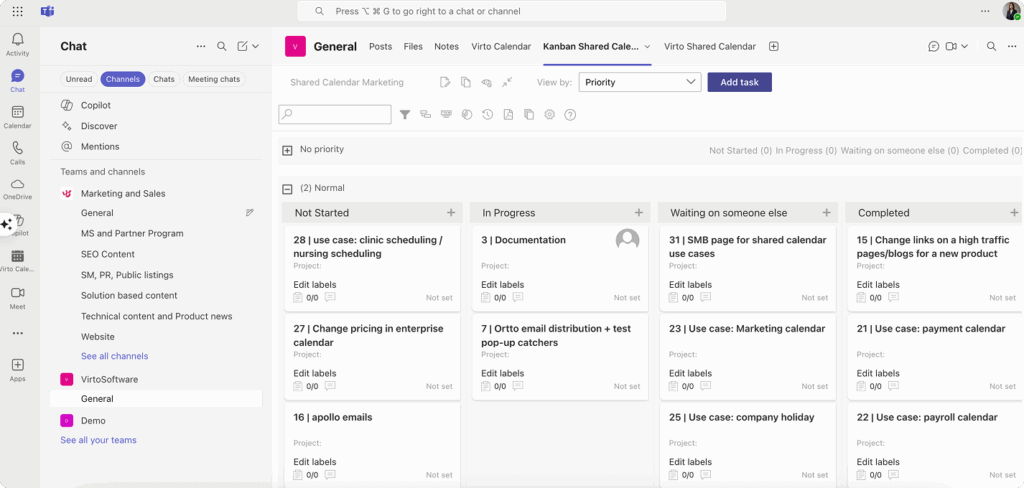
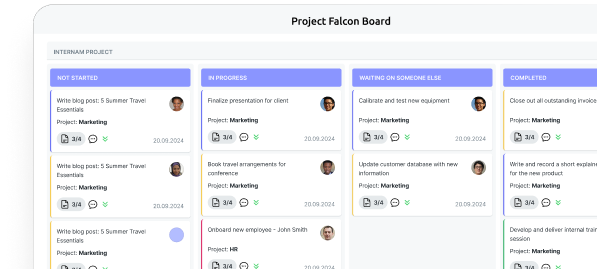
Virto Kanban Board for Teams delivers project management capabilities directly within Teams channels. The application supports agile workflows, progress tracking, and capacity management without requiring users to switch between applications. Administrative controls allow for board management, user permissions, and integration with existing Teams structures.
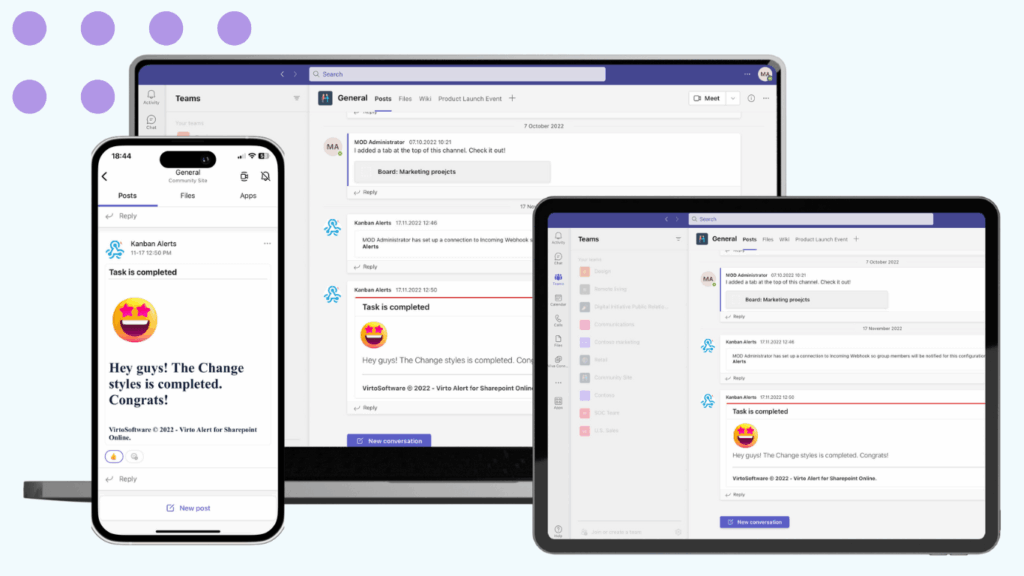
Virto Notifications & Reminders App enables automated alert systems and scheduled notifications within Teams. This application supports webhook integrations, condition-based alerts, and SharePoint list monitoring. Administrators can configure organization-wide notification policies while maintaining granular control over alert delivery and escalation procedures.
Virto Polls for Teams is currently under development and promises to significantly enhance Microsoft Teams polling functionality. This upcoming application will provide advanced polling capabilities beyond Teams’ basic voting features, offering administrators more sophisticated tools for gathering feedback, conducting surveys, and facilitating decision-making processes within Teams environments.
| Application | Primary function | Key features | Best for |
| Virto Shared Calendar | Event sharing | Anonymous access, color coding | External collaboration |
| Virto Calendar App | Calendar overlay | Multi-source integration, views | Unified scheduling |
| Virto Kanban Board | Project management | Agile workflows, progress tracking | Team productivity |
| Virto Notifications | Alert automation | Webhook integration, conditions | Process automation |
| Virto Polls (Coming) | Advanced polling | Enhanced voting features | Decision making |
All VirtoSoftware applications comply with enterprise security requirements and integrate with existing Teams administrative policies. These tools undergo regular security audits and maintain compatibility with Microsoft’s evolving Teams platform. Administrators can evaluate these solutions through free trials available directly from the Microsoft Teams App Store or the VirtoSoftware website.
Organizations interested in exploring these productivity enhancements can schedule demonstration calls to assess specific use cases and integration requirements. The applications provide additional functionality while preserving the administrative control and security standards that Teams administrators require for their enterprise environments.
Conclusion on Admin Center Teams
The Microsoft Teams Admin Center stands as a critical tool for managing your corporate Teams environment effectively. The difference between a well-administered Teams deployment and a chaotic one often comes down to how thoroughly administrators understand and utilize these administrative capabilities.
Properly configuring the Admin Center helps ensure security, efficiency, and ease of use across your Teams implementation. The policies you set, the monitoring you establish, and the training you provide create the foundation for productive collaboration while maintaining the security standards your organization requires.
The continuous evolution of the Admin Center reflects Microsoft’s commitment to addressing real-world administrative challenges. The 2024 introduction of unified settings and policies management demonstrates how administrative feedback drives meaningful improvements that reduce complexity and improve efficiency. Similarly, the upcoming AI assistant capabilities and enhanced security features show Microsoft’s focus on proactive administration rather than reactive problem-solving.
Consider exploring additional VirtoSoftware applications that extend the standard capabilities of Teams and can significantly simplify the work of administrators. These productivity tools integrate directly with Teams while maintaining enterprise-grade security and administrative control. Schedule a quick demo call to learn more and ask questions about how these apps might benefit your specific environment. Alternatively, install free trials directly from the Microsoft Teams App Store by searching for specific applications like Virto Calendar or Virto Kanban Board, or visit the VirtoSoftware website to explore the complete suite of available tools.
For continued learning and deeper expertise, peruse these additional resources:
Official Microsoft resources:
- Manage teams in the modern portal
- Manage apps in Teams
- Manage admin app settings
- Microsoft 365 administration overview
Additional resources from VirtoSoftware:
Regular configuration audits, proactive policy management, and continuous user education form the foundation of effective Teams administration. These practices, combined with proper use of the Admin Center’s extensive capabilities, create sustainable Teams deployments that grow with organizational needs rather than constraining them.
Bottom line: Master the Teams Admin Center, implement consistent policies, train your users, and monitor your environment regularly. Your organization’s productivity and security depend on getting these fundamentals right.