SharePoint Security: Complete Guide for Safe Collaboration
This comprehensive security guide walks you through protecting your SharePoint environment with current patches, modern authentication methods, and proven access controls that actually work—not the outdated advice that dominates most documentation.
Corporate data security demands more than good intentions. It requires systematic controls, regular audits, and a clear understanding of where vulnerabilities hide. SharePoint, Microsoft’s collaboration and document management platform, processes millions of sensitive files daily across organizations worldwide. The platform’s security architecture goes beyond basic file storage, incorporating authentication layers, granular permissions, and encryption protocols that work together to protect organizational data.
Recent events underscore why SharePoint security matters now more than ever. In July 2025, attackers actively exploited vulnerabilities in SharePoint Server installations, forcing Microsoft to issue emergency patches and detailed remediation guidance. These attacks targeted on-premises deployments specifically, leaving SharePoint Online customers unaffected but highlighting the critical differences between cloud and self-hosted security models.
This guide examines SharePoint’s security mechanisms, identifies common configuration errors that create vulnerabilities, and provides specific steps to protect your environment. You’ll learn how to configure access controls properly, implement Microsoft’s latest security features, and avoid the mistakes that lead to data breaches. The recommendations here apply to both SharePoint Online and SharePoint Server deployments, with clear distinctions made where their security requirements diverge.
We’ll also address the practical challenges organizations face: managing external sharing without creating security gaps, balancing collaboration needs with data protection requirements, and maintaining security as your SharePoint environment grows. Each section includes actionable steps you can implement immediately, along with guidance on using specialized tools to enhance SharePoint’s native security capabilities.
What Is SharePoint Security?
SharePoint security encompasses the organizational and technical measures that protect corporate data, control user access, and secure integrations across the Microsoft 365 ecosystem. Rather than treating security as an add-on feature, SharePoint builds protection directly into its architecture through multiple defensive layers that work together to safeguard information assets.
At its core, SharePoint security protects three critical elements:
- It secures corporate data including files, documents, and entire libraries from unauthorized access or modification.
- It manages user access to sites and workspaces through granular permission systems.
- It protects integrations with other Microsoft 365 services and external applications, ensuring data remains secure as it moves between systems.
Microsoft implements this protection through a multi-layered security model.
- Authentication verifies user identity through passwords, multi-factor authentication, and Single Sign-On via Microsoft Entra ID (formerly Azure Active Directory) for cloud deployments or Active Directory for on-premises installations.
- Authorization then determines what authenticated users can actually do, distributing access rights at multiple levels: sites, libraries, folders, and individual documents. Every action gets recorded through comprehensive auditing and monitoring systems that log user activities, document changes, and access attempts.
- Finally, encryption protects data both in transit using SSL/TLS protocols and at rest through database encryption and file storage protection.
This layered approach means that even if one security measure fails, others continue protecting your data. A compromised password, for instance, gets stopped by multi-factor authentication. An authorized user attempting to access restricted content gets blocked by granular permissions. Suspicious activity patterns trigger alerts through the monitoring system before damage occurs.
How secure is SharePoint?
SharePoint provides enterprise-grade security when configured properly and maintained according to Microsoft’s recommendations. The platform’s security depends heavily on implementation choices. Organizations that enable multi-factor authentication, configure appropriate permission levels, and regularly audit access achieve strong security outcomes. Those that skip these steps or misconfigure settings create vulnerabilities that attackers can exploit.
Is SharePoint more secure than OneDrive?
SharePoint and OneDrive use identical Microsoft data protection technologies, including the same encryption standards and authentication mechanisms. The distinction lies in their administrative capabilities and intended use cases. SharePoint offers more sophisticated tools for access control, automation, and collaboration management. Administrators can create complex permission hierarchies, implement conditional access policies, and enforce data governance rules across entire departments. These capabilities make SharePoint better suited for organizations managing sensitive projects, regulatory compliance, or large-scale collaboration. OneDrive excels at personal file storage and small team sharing but lacks the granular controls necessary for enterprise-wide data governance.
The security model’s effectiveness becomes clear when examining real-world usage:
- Financial institutions use SharePoint’s permission inheritance and breaking capabilities to ensure deal documents remain accessible only to specific teams.
- Healthcare organizations leverage its audit logs to demonstrate HIPAA compliance.
- Educational institutions apply different security policies to student records versus public content.
These scenarios require SharePoint’s advanced security features that extend beyond OneDrive’s simpler sharing model.
| Feature | SharePoint | OneDrive |
| Permission levels | Granular (site, library, folder, item) | Simple (file and folder only) |
| External sharing controls | Advanced policies, expiration dates, guest groups | Basic sharing links |
| Audit capabilities | Comprehensive logs, detailed reports | Limited activity tracking |
| Compliance tools | DLP policies, retention rules, eDiscovery | Basic retention only |
| Best for | Enterprise collaboration, regulated data | Personal files, small team sharing |
💡 Learn more about SharePoint vs OneDrive in a dedicated piece: OneDrive vs SharePoint: Key Differences Explained
Key SharePoint Security Features
SharePoint’s security framework relies on several interconnected features that protect data at different levels. Each component addresses specific vulnerabilities while contributing to the platform’s overall defensive posture.
User authentication
Security in SharePoint begins with verifying user identity through enterprise-grade authentication mechanisms.
- SharePoint Online leverages Microsoft Entra ID (formerly Azure Active Directory) to provide single sign-on (SSO), multi-factor authentication (MFA), and conditional access policies. These features work together to ensure only legitimate users gain system access.
- On-premises deployments integrate with Active Directory to manage accounts within the organization’s existing infrastructure.
Administrators can configure authentication requirements based on risk levels. Accessing routine documents might require only standard authentication, while viewing confidential financial data triggers additional verification steps. Conditional access policies add another layer by evaluating factors like user location, device compliance, and network security before granting access. A login attempt from an unrecognized device or suspicious geographic location automatically triggers enhanced authentication requirements or blocks access entirely.
👉Is SharePoint secure? SharePoint provides enterprise-grade security features including encryption, granular permissions, and comprehensive auditing, but its actual security depends entirely on proper configuration and maintenance. SharePoint Online offers stronger default protection through automatic patching and Microsoft’s security infrastructure, while on-premises deployments require significant expertise to achieve equivalent security levels. The platform is secure when organizations enable MFA, configure appropriate permissions, maintain current patches, and train users properly; without these measures, even SharePoint’s robust security architecture cannot protect against breaches.
Flexible access rights management
SharePoint’s permission system operates through three interconnected components: permissions, roles, and scopes:
- Individual permissions control specific actions like viewing, editing, or deleting content.
- Roles combine multiple permissions into logical groups such as Visitors (read-only access), Members (contribute and edit), and Owners (full control including permission management).
- Scopes determine where these permissions apply, from entire site collections down to individual documents.
This granular control distinguishes SharePoint from simpler storage solutions.
- A legal department, for example, can grant partners read access to specific contract folders while preventing downloads of sensitive attachments.
- Project managers can allow team members to edit project documents while restricting access to budget files within the same library.
The system supports both inherited permissions that flow from parent to child objects and unique permissions for exceptional cases.
Breaking permission inheritance should be done sparingly and strategically. Each unique permission creates additional administrative overhead and increases the risk of access control errors. Organizations achieve better security outcomes by structuring their SharePoint architecture to minimize inheritance breaks, using separate sites or libraries for content requiring different access levels.
Version control and user auditing
SharePoint automatically maintains document version history, creating snapshots each time users save changes. This versioning system serves multiple security purposes beyond simple revision tracking. When ransomware attacks encrypt files or users accidentally delete content, administrators can restore previous versions immediately. Version limits prevent storage bloat while maintaining sufficient history for recovery and compliance needs.
The audit logging system records extensive detail about user activities. Every document access, modification, download, and permission change gets logged with timestamps and user identification. SharePoint captures who opened specific documents, what changes they made, when they shared content externally, and which permissions they modified. Organizations using SharePoint Advanced Management can now delegate oversharing remediation to site owners through site access reviews, distributing the security monitoring workload while maintaining central oversight.
These audit capabilities prove essential for regulatory compliance and security investigations.
- Healthcare organizations demonstrate HIPAA compliance by showing who accessed patient records.
- Financial institutions track document access for insider trading investigations.
- Educational institutions monitor student record access to ensure privacy compliance.
Encryption of data at rest and in transit
SharePoint implements encryption at multiple levels to protect data regardless of its state. During transmission, all connections use TLS encryption to prevent interception or tampering. This protection applies whether users access SharePoint through web browsers, mobile apps, or desktop clients.
For data at rest, SharePoint Online encrypts all files using unique per-file keys exclusive to each tenant, with BitLocker providing additional disk-level encryption. Organizations requiring additional control can implement Customer Key, which allows them to manage the root encryption keys used by the service.
On-premises deployments must manually configure SSL certificates and enable SQL Server Transparent Data Encryption to achieve similar protection levels.
The encryption architecture ensures that even if attackers gain physical access to Microsoft’s data centers or steal backup media, the data remains unreadable without the corresponding encryption keys. Microsoft’s key management system separates keys from data, stores them in hardened key vaults, and rotates them regularly according to security best practices.
Configure data retention and deletion policies
SharePoint’s retention capabilities help organizations balance data preservation requirements with security and compliance needs. Administrators can configure policies that automatically delete obsolete documents after specified periods, reducing the attack surface and limiting potential breach exposure. Conversely, policies can preserve legally significant documents for required retention periods, preventing premature deletion that could result in compliance violations.
Microsoft Purview portal (formerly the Compliance Center) provides centralized retention management across SharePoint and other Microsoft 365 services. Organizations can create policies based on content types, sensitivity labels, or specific metadata values.
- A healthcare provider might retain patient records for seven years while automatically purging administrative documents after two years.
- Law firms can place legal holds on case-related documents while allowing routine correspondence to follow standard deletion schedules.
Retention policies work alongside sensitivity labels to create comprehensive information governance. When organizations enable sensitivity label support for SharePoint and OneDrive, they can process encrypted Office and PDF files while maintaining full indexing and auditing capabilities. Libraries can apply default sensitivity labels automatically, ensuring consistent protection for new documents. The “extend permissions on download” feature maintains SharePoint access controls even after users download files locally, reducing the risk of unauthorized sharing.
👉 What are the biggest threats to SharePoint data security? The most dangerous threats are incorrectly configured permissions—especially “Anyone with the link” sharing and broken inheritance that accumulates over time—which expose sensitive data far beyond intended audiences. Unpatched on-premises servers create critical vulnerabilities that attackers actively exploit. Compromised user credentials from phishing attacks bypass technical controls entirely, giving attackers legitimate access to exfiltrate data, modify permissions for persistent access, and launch internal attacks that appear credible because they originate from trusted accounts.
SharePoint Online and On-Premise Security Features
The choice between SharePoint Online and On-Premise deployments fundamentally shapes an organization’s security responsibilities and capabilities. Each model offers distinct advantages, and understanding their differences helps organizations select the appropriate platform for their security requirements.
SharePoint Online security: cloud-based protection
SharePoint Online operates as a fully managed service within Microsoft’s cloud infrastructure, where Microsoft handles the underlying security operations. Security updates and patches install automatically without administrative intervention, often within hours of discovery. This rapid response proved critical during recent vulnerability discoveries, as SharePoint Online customers remained protected while on-premises installations required manual patching.
Microsoft’s infrastructure employs defense-in-depth strategies including network segmentation, intrusion detection and prevention systems (IDS/IPS), and continuous security monitoring across all data centers. The platform undergoes regular third-party audits for compliance certifications including ISO 27001, SOC 2, and FedRAMP, providing independent verification of security controls.
Built-in security mechanisms extend beyond basic protection. Data Loss Prevention (DLP) policies identify and block transmission of sensitive information such as credit card numbers, social security numbers, or custom-defined data patterns. The Microsoft Purview portal centralizes compliance management, enabling organizations to implement retention policies, eDiscovery holds, and regulatory compliance controls from a single interface. Conditional Access policies evaluate multiple signals before granting access, including user risk levels, device compliance status, application sensitivity, and network location.
Multi-factor authentication comes standard for all Microsoft 365 users, requiring minimal configuration to activate. Organizations can enforce MFA selectively based on user roles, gradually expanding coverage to minimize disruption. Advanced authentication methods include passwordless options using Windows Hello, FIDO2 security keys, or the Microsoft Authenticator app, providing both enhanced security and improved user experience.
The benefits for organizations are substantial. IT departments avoid the complexity of managing server infrastructure, applying security patches, and maintaining high availability. Rapid deployment allows organizations to establish secure collaboration environments within days rather than months. Microsoft’s global infrastructure provides built-in redundancy, distributed data centers, and a 99.9% uptime SLA that most organizations cannot achieve independently.
Recent enhancements allow granular control over unmanaged devices, with policies now supporting block or limited access configurations by user, group, and individual site. Organizations can restrict downloads from personal devices while permitting web-only access, balancing productivity with data protection.
SharePoint On-Premise security: maintaining control
SharePoint On-Premise deployments run on organization-managed servers, providing complete control over the security configuration. Administrators determine patch schedules, configure firewalls, and implement security policies according to organizational requirements. This control comes with significant responsibility, as demonstrated by the July 2025 attacks that exploited unpatched SharePoint Server installations through CVE-2025-53770 and CVE-2025-53771.
The flexibility of on-premises deployments allows extensive customization. Organizations can implement air-gapped networks completely isolated from the internet, custom authentication providers integrated with proprietary systems, or specialized encryption mechanisms required by regulatory frameworks. Security teams maintain direct access to logs, databases, and configuration files, enabling detailed forensic analysis and custom monitoring solutions.
However, this flexibility demands substantial expertise and resources. Security teams must actively monitor Microsoft’s security bulletins, test patches in development environments, and coordinate maintenance windows for production updates. The July 2025 incidents highlighted these challenges when organizations struggled to implement Microsoft’s emergency patches, rotate ASP.NET machine keys, enable AMSI (Anti-Malware Scan Interface) in full mode, and restart IIS services across their server farms.
Beyond SharePoint itself, administrators must secure the entire stack. This includes hardening Windows Server, configuring SQL Server encryption, managing SSL certificates, implementing network segmentation, and maintaining backup systems. Each component represents a potential attack vector if misconfigured or left unpatched. Recent vulnerabilities included CVE-2024-30044 patched in May 2024, CVE-2024-38094 addressed in July 2024, and CVE-2024-49070 fixed in December 2024, all requiring manual intervention to protect on-premises installations.
When to use each deployment model
SharePoint On-Premise suits organizations with specific regulatory requirements that mandate data residency within national borders or complete infrastructure control. Government agencies handling classified information, healthcare organizations processing sensitive patient data in jurisdictions with strict localization laws, and financial institutions with legacy system dependencies often require on-premises deployments. Defense contractors working with ITAR-controlled data frequently cannot use cloud services regardless of their security certifications.
The on-premises model also accommodates organizations with existing investments in data center infrastructure, specialized security appliances, or custom-developed solutions that cannot migrate to the cloud. Some manufacturing companies operate in locations with unreliable internet connectivity, making cloud services impractical for daily operations.
SharePoint Online better serves organizations prioritizing rapid deployment, predictable costs, and reduced administrative overhead. Startups and growing companies benefit from enterprise-grade security without building internal expertise. Multinational corporations leverage Microsoft’s global infrastructure to provide consistent performance across geographic regions. Organizations focusing on core business activities rather than IT infrastructure management find the managed service model more cost-effective when considering total ownership costs including hardware, software, personnel, and ongoing maintenance.
The security implications of each model extend beyond technical considerations. SharePoint Online customers benefit from Microsoft’s massive security investments, threat intelligence networks, and immediate response to emerging threats. On-premises deployments offer complete control but require equivalent security expertise and operational discipline to achieve comparable protection levels. Organizations must honestly assess their capabilities before choosing the deployment model that best balances their security requirements with available resources.
| Area | Update | Why it matters | Effective / Published | What to do | Where to learn more |
| SharePoint Server (on-prem) | “ToolShell” zero-days: CVE-2025-53770 & CVE-2025-53771 actively exploited | Real-world compromises against Internet-facing farms; Microsoft shipped emergency updates plus hardening guidance | Jul 19–22, 2025 | Patch immediately; enable AMSI (Full Mode); rotate ASP.NET machineKey; deploy EDR | Microsoft MSRC guidance & Microsoft Security Blog. (Microsoft Security Response Center, Microsoft) |
| SharePoint Server (on-prem) | 2024 post-auth RCE (CVE-2024-38094) exploited in the wild | Long-tail risk for unpatched 2016/2019/SE farms | Jul 2024 (patch); exploitation noted Oct 2024 | Verify July 2024 CU applied; review logs for web shells | CISA/industry advisories. (SecurityWeek, broadcom.com) |
| SharePoint Server (on-prem) | AMSI integration & admin UI (SE 25H1) | Lets your AV inspect HTTP/S request bodies and block malicious payloads before SharePoint processes them | Mar 2025 (SE 25H1 UI); default enablement referenced in 2025 MSRC post | Confirm AMSI enabled on all web apps; use “Full Mode”; validate health | Microsoft Learn (AMSI config) & MSRC guidance. (Microsoft Learn, Microsoft Security Response Center) |
| SharePoint Online | OTP external sharing links retired in favor of Entra ID B2B | Legacy OTP links stop working; guests must sign in as B2B | Jul 1, 2025 | Inventory impacted links; reshare via B2B; update user comms | Microsoft Learn (Entra B2B integration FAQ) & Microsoft community note. (Microsoft Learn, TECHCOMMUNITY.MICROSOFT.COM) |
| SharePoint Online | Classic Alerts are retiring (move to Rules/Power Automate) | Old notification method phases out; potential user confusion if not planned | Timeline: new tenants blocked Jul 2025; all tenants blocked Jan 2026; feature removed Jul 2026 | Replace with Rules/Power Automate; update training/helpdesk | Microsoft Support retirement notice. (Microsoft Support) |
| SharePoint Online | Sensitivity labels for encrypted Office & PDFs fully processed in SPO/OneDrive | Enables coauthoring, eDiscovery, search & DLP even when content is label-encrypted | Updated Aug 7, 2025 | Enable label support for Office/PDF; verify clients; plan auto-labeling | Microsoft Learn. (Microsoft Learn) |
| SharePoint Online | Default library label + Extend protection on download/copy/move | Lets site owners auto-label content and carry site permissions with files leaving SharePoint | Default label doc updated Jun 10, 2025; “extend permissions” feature | Set default label; consider “extend protection” for sensitive libs | Microsoft Learn (default label & extend permissions). (Microsoft Learn) |
| SharePoint Online | Unmanaged device controls (block or web-only) with fine scoping | Limits data egress from personal devices; can target specific users/sites | Guidance updated Apr 17, 2025 | Pair with Conditional Access; apply to high-risk sites first | Microsoft Learn. (Microsoft Learn) |
| SharePoint Online (Governance) | SharePoint Advanced Management (SAM): Data Access Governance reports & Site Access Reviews | Owner-driven remediation for oversharing; ongoing exposure reduction | SAM overview updated Jun 30, 2025; site reviews doc Aug 28, 2025 | Run DAG reports; initiate access reviews on overshared sites | Microsoft Learn (SAM & reviews). (Microsoft Learn) |
| SharePoint/OneDrive/Teams | Safe Attachments for SPO/OneDrive/Teams improvements | Detonates & locks malicious files in libraries; integrates with Defender reports | Docs refreshed Jul–Aug 2025 | Turn on Safe Attachments; optionally block downloads of detected files | Microsoft Learn. (Microsoft Learn) |
| Microsoft Purview (Endpoints) | Endpoint DLP Just-in-Time (JIT) protection | Temporarily blocks egress while policy evaluates—closing DLP “race conditions” | Docs updated Mar 31, 2025 & Jul 11, 2025 | Enable JIT for scoped users/devices; test user experience | Microsoft Learn. (Microsoft Learn) |
| Microsoft Purview (DLP) | New Data Classification Content Download role for evidence | Tighter RBAC for downloading endpoint evidence from Activity Explorer/DLP alerts | Rollout Mar–Apr 2025 | Assign only to investigators; review evidence handling SOPs | Microsoft Learn & rollout notice. (Microsoft Learn) |
SharePoint Vulnerabilities and Risks
SharePoint’s security depends as much on proper configuration and maintenance as on its built-in protections. Most breaches result from preventable mistakes rather than platform flaws, making it crucial to understand where vulnerabilities typically emerge.
Incorrectly configured access rights
Excessive permissions remain the most common security threat in SharePoint deployments. Users frequently receive edit access when read-only permissions would suffice, or administrators grant full control rights for temporary tasks without revoking them afterward. These accumulated permissions create pathways for data exposure that grow more dangerous over time.
Permission inheritance errors compound the problem. A site owner might break inheritance to restrict access to a sensitive library, unknowingly granting broader permissions at the site level that cascade down to supposedly protected content. External sharing amplifies these risks exponentially. “Anyone with the link” sharing options, while convenient for collaboration, can expose corporate documents to the entire internet if URLs leak through forwarded emails, compromised accounts, or simple user error.
Microsoft addressed one aspect of this risk when legacy one-time passcode (OTP) external sharing links stopped working on July 1, 2025, forcing organizations to reshare content using more secure Entra ID B2B guest access. However, many organizations discovered they had thousands of active external shares they weren’t tracking, highlighting the scope of unmanaged access proliferation.
💡Learn more about secure sharing in SharePoint in our dedicated pieces:
- SharePoint Share with External Users: Best Practices for Collaborating
- SharePoint Secure File Sharing: Methods, Best Practices, and Advanced Tips
Outdated versions of SharePoint On-Premise
On-premises SharePoint installations face continuous security threats from unpatched vulnerabilities. As mentioned earlier, the July 2025 attacks exploiting CVE-2025-53770 and CVE-2025-53771 demonstrated how quickly adversaries weaponize disclosed vulnerabilities. Organizations had mere days between Microsoft’s security advisory and active exploitation in the wild. Those without robust patch management processes found themselves racing to apply fixes while potentially already compromised.
The attack chain often extends beyond SharePoint itself. Vulnerabilities in underlying components like IIS, SQL Server, or .NET Framework can provide initial access that attackers escalate to compromise SharePoint. Legacy authentication protocols, outdated SSL certificates, and misconfigured firewall rules create additional entry points. Each component requires individual attention, turning patch management into a complex orchestration challenge.
Historical data reveals a pattern of escalating risks for unpatched systems. CVE-2024-30044 from May 2024 allowed remote code execution, while CVE-2024-38094 and CVE-2024-49070 added additional attack vectors throughout 2024. Organizations that delayed patching accumulated multiple vulnerabilities, creating increasingly attractive targets for attackers.
Phishing attacks and stolen credentials
Human psychology remains the weakest link in SharePoint security. Sophisticated phishing campaigns specifically target SharePoint users with fake document sharing notifications that mirror legitimate SharePoint emails. Users click malicious links believing they’re accessing shared files from colleagues, inadvertently providing credentials to attackers.
Without multi-factor authentication, a single compromised account grants attackers legitimate access to all resources available to that user. They can exfiltrate sensitive documents, modify critical files, or use the account to launch internal phishing campaigns that appear even more credible. Advanced persistent threats often maintain access for months, slowly extracting data while avoiding detection through normal-appearing activity patterns.
Account compromise impacts extend beyond immediate data theft. Attackers modify sharing permissions to maintain access after password resets, create new external sharing links for future access, or plant malicious files that exploit client-side vulnerabilities. Recovery requires not just password changes but comprehensive audits of all permissions, shares, and content modified during the compromise period.
Integrating third-party solutions without security verification
SharePoint’s extensibility through web parts, apps, and custom solutions introduces security risks when organizations deploy unvetted third-party code. Marketplace apps might request excessive permissions, accessing data beyond their functional requirements. Custom-developed solutions often contain security flaws from inexperienced developers unfamiliar with SharePoint security best practices.
Legacy web parts pose particular risks in on-premises environments. Code written for older SharePoint versions may use deprecated APIs, bypass security checks, or contain known vulnerabilities. Organizations often maintain these components because they provide critical functionality, creating technical debt that accumulates security risk over time. Server-side code with elevated privileges can access any data within the farm, making a single vulnerable web part capable of compromising the entire SharePoint deployment.
Even modern SharePoint Framework (SPFx) solutions require careful review. While operating within a sandboxed environment, poorly written SPFx components can still expose sensitive data through client-side vulnerabilities, excessive API permissions, or insecure external service integrations. Organizations must evaluate whether third-party solutions undergo regular security audits, how vendors respond to vulnerability disclosures, and what data access the solutions actually require versus request.
What are the security concerns of SharePoint?
The primary security concerns cluster around three areas: data leaks, unauthorized access, and human factors. Data leaks occur through public sharing links distributed too broadly, synchronization to unmanaged devices, or external collaboration without proper controls. Unauthorized access results from permission creep, inheritance errors, or compromised credentials. Human factors include phishing susceptibility, poor password practices, and circumvention of security policies for convenience.
These concerns intensify with organizational growth. Small deployments with few users and simple permission structures can maintain security through manual oversight. Enterprise deployments with thousands of users, complex organizational hierarchies, and extensive external collaboration require automated controls, regular audits, and comprehensive security policies. Security degrades gradually as permissions accumulate, external shares proliferate, and configuration drift occurs without regular review.
Organizations must also consider supply chain risks. Partners, vendors, and customers with SharePoint access represent extended attack surfaces. A compromise at a third-party organization can provide attackers with legitimate credentials to access your SharePoint environment. SharePoint Advanced Management’s site access reviews help identify and remediate these expanding access patterns, but organizations must proactively manage external access rather than reactively responding to incidents.

👉What is SharePoint data protection? SharePoint data protection encompasses the technical and administrative controls that safeguard information throughout its lifecycle: encryption using unique per-file keys for data at rest and TLS for data in transit, granular permission systems that control access from site collections down to individual documents, and comprehensive audit logging that tracks every user action. Microsoft Purview extends these protections through Data Loss Prevention policies that prevent sensitive information from leaving organizational boundaries, retention rules that automatically preserve or delete content according to compliance requirements, and sensitivity labels that maintain protection even after files leave SharePoint. These layered defenses work together to protect against unauthorized access, accidental exposure, regulatory violations, and data loss, whether from external attacks, insider threats, or simple user error.
Access Management and Security Best Practices
Effective Microsoft SharePoint security combines technical controls with practical implementation strategies. While the platform provides extensive security features, their value depends entirely on how organizations deploy and manage them. The following best practices transform SharePoint’s security capabilities from theoretical protections into operational safeguards that protect your data without impeding collaboration. These guidelines apply whether you’re securing a single team site or managing an enterprise-wide deployment.
How do I secure a SharePoint site?
Securing a SharePoint site requires systematic implementation of access controls, technical safeguards, and ongoing maintenance procedures. The process begins with understanding SharePoint’s permission hierarchy and applying security measures at each level.
Access hierarchy in SharePoint
SharePoint’s security boundaries follow a clear hierarchy: site collections contain sites, which contain libraries and lists, which contain folders and individual items. Permissions typically flow downward through inheritance, with each level receiving the access rights of its parent unless you explicitly break inheritance.
The site level serves as your primary security boundary. Most organizations achieve optimal security by designing their site structure to match their security requirements, rather than retroactively applying complex permission schemes. A marketing department might maintain separate sites for public content, internal campaigns, and agency collaboration, each with appropriate baseline permissions.
Libraries and lists provide the next control point, allowing different permissions for various content types within a site. Folders offer additional granularity but increase administrative complexity. Setting permissions at the individual document level should remain rare; if you frequently need item-level permissions, your architecture likely needs restructuring.
SharePoint includes built-in roles that simplify permission management. Visitors receive read-only access, Members can add and edit content, while Owners control permissions and settings. Custom permission levels address specific needs, but each additional level increases complexity. Most organizations operate effectively with the default roles plus one or two custom levels for specialized scenarios.
💡 Learn more about document management in SharePoint in our dedicated articles:
- How to Create and Manage a SharePoint Document Library
- Optimize Your Business with SharePoint Document Management
- Best Practices for SharePoint Document Management, Library, Folder Structure and Security
Setting permissions
The principle of least privilege should guide every permission decision. Users receive only the minimum access required for their responsibilities, with permissions expanding temporarily for specific projects then reverting afterward. This approach limits potential damage from compromised accounts and reduces accidental data exposure.
Permission inheritance streamlines administration when used properly. Default inheritance from parent objects works well for most content, with inheritance breaks reserved for genuine exceptions. Rather than breaking inheritance throughout your hierarchy, structure your SharePoint architecture so that content with different security requirements resides in separate sites or libraries. A single library with fifty unique permissions becomes an administrative nightmare and audit challenge.
Group-based permissions provide scalability and consistency. Instead of assigning permissions to individual users, create groups aligned with job functions or project teams. Use Microsoft Entra ID security groups for enterprise-wide roles and SharePoint groups for site-specific access. When employees change roles, updating their group membership automatically adjusts all associated permissions.
External users require special consideration. Guest access should flow through dedicated external collaboration sites with restricted permissions and mandatory expiration dates. The new requirement to use Entra ID B2B guest access instead of one-time passcodes provides better control and auditing capabilities. Configure sharing settings to prevent guests from resharing content and require owner approval for access extensions.
Document your permission model using a simple matrix showing roles, rights, and scopes. This documentation proves invaluable during audits, troubleshooting, and onboarding new administrators. Include decision criteria for breaking inheritance, creating custom permission levels, and granting external access.
💡 Learn more about permission management in our article: Configuration & Management of SharePoint Permissions: A Complete Guide 2025

Technical security measures
Multi-factor authentication forms your first technical defense. Every user, particularly administrators and those accessing sensitive data, must use MFA. SharePoint Online enables MFA through Microsoft Entra ID with minimal configuration. On-premises deployments require Active Directory Federation Services (ADFS) or third-party authentication providers. Modern authentication methods like passwordless sign-in using Windows Hello or FIDO2 keys provide both enhanced security and improved user experience.

Encryption protects data throughout its lifecycle. As mentioned, SharePoint Online automatically encrypts files using unique per-file keys exclusive to each tenant, with BitLocker providing additional disk-level encryption and TLS securing data in transit. On-premises administrators must manually configure SSL certificates for transport security and enable Transparent Data Encryption for SQL Server databases. Regular certificate updates prevent expiration-related outages that could force security bypasses.
Sensitivity labels extend protection beyond SharePoint’s boundaries. Once enabled for SharePoint and OneDrive, these labels can process encrypted Office and PDF files while maintaining search and coauthoring capabilities. Apply default labels to sensitive libraries, ensuring consistent protection for new content. The “extend permissions on download” feature maintains SharePoint access controls even after users save files locally, preventing unauthorized sharing through other channels.
Audit and activity monitoring
SharePoint’s audit logs capture extensive operational detail: every login, file access, modification, download, deletion, and permission change. These logs serve multiple purposes from security investigations to compliance demonstrations. Configure log retention based on your regulatory requirements and investigation needs, typically between 90 days and 7 years.
Active monitoring transforms logs from forensic tools into prevention mechanisms. Configure alerts for anomalous activities like mass downloads, unusual deletion patterns, or permission escalations. Microsoft Purview’s DLP alerts replace the retiring SharePoint Alerts feature, providing more sophisticated detection capabilities. Set thresholds that balance security with operational noise; too many false positives lead to alert fatigue and missed genuine threats.
The new Data Classification Content Download role in Purview allows controlled access to evidence from Activity Explorer and DLP alerts, enabling security teams to investigate incidents without exposing sensitive data unnecessarily. This granular control proves essential for organizations with dedicated security operations centers or compliance teams.
Regular access reviews
Permissions naturally accumulate over time as users join projects, receive temporary access, and change roles. Quarterly access reviews by site owners identify and remove unnecessary permissions before they become security liabilities. Focus reviews on high-risk areas: external shares, sites containing sensitive data, and users with elevated privileges.
SharePoint Advanced Management’s site access reviews automate much of this process, sending targeted remediation tasks to site owners based on data governance reports. Site owners receive notifications about overshared content, stale guest accounts, and unusual permission patterns, distributing the security workload while maintaining central oversight.
Administrators should conduct comprehensive audits semi-annually, examining broken inheritance patterns, custom permission levels, and service account access. Look for permission creep indicators: users with access to sites outside their department, former employees’ accounts still active through group membership, and external shares older than your collaboration policy permits. Document findings and remediation actions to track security posture improvements over time.
Automation reduces review burden while improving consistency. Microsoft Entra ID Access Reviews can automatically remove users from groups after specified periods without manual intervention. Power Automate flows can notify owners about expiring guest access or flag sites that haven’t been reviewed recently. The investment in automation setup pays dividends through reduced administrative overhead and improved security compliance.
💡 Learn more about SharePoint automation in our dedicated piece:
SharePoint Automation: Best Practices, Use Cases and Recommended Tools

Collaboration and Security Management
Security in SharePoint succeeds only when administrators, site owners, and end users understand their respective responsibilities and work together toward common protection goals. Technical controls provide the foundation, but human behavior determines whether those controls effectively protect organizational data.
SharePoint and Microsoft 365 administrators
Administrators establish the security framework within which all SharePoint activity occurs. They configure tenant-wide policies that set baseline security standards: mandatory multi-factor authentication, conditional access rules based on risk signals, and Data Loss Prevention policies that prevent sensitive information from leaving organizational boundaries. These global settings create guardrails that protect against common mistakes while allowing flexibility for legitimate business needs.
Beyond initial configuration, administrators maintain the security infrastructure through regular updates, monitoring, and adjustment. They analyze audit logs for unusual patterns, investigate security alerts, and respond to emerging threats.
External access and third-party integrations require particular administrative attention. Administrators must balance collaboration needs with security requirements, enabling productive external partnerships while preventing data exposure. This includes configuring guest access policies, reviewing OAuth permissions for integrated applications, and monitoring unusual external sharing patterns that might indicate compromise or policy violations.
Site owners
Site owners serve as the first line of defense for their content areas. They translate organizational security policies into practical implementation within their sites, making daily decisions about who needs access, what permissions they require, and how long that access should persist. This distributed responsibility model scales security management across large organizations while maintaining local accountability.
Creating and maintaining appropriate user groups forms a core site owner responsibility. Rather than granting ad-hoc permissions to individuals, site owners should establish groups aligned with functional roles: project contributors, external reviewers, read-only stakeholders. When team composition changes, updating group membership automatically adjusts access across all associated content.
Site owners bear responsibility for regular permission audits within their domains. SharePoint Advanced Management’s site access reviews streamline this process by automatically identifying overshared content and generating remediation tasks. A quarterly review might reveal that project folders still grant access to contractors whose engagements ended months ago, or that sensitive documents inadvertently inherited broader permissions from their parent library.
The decision to break permission inheritance requires careful consideration. Each unique permission creates ongoing administrative overhead and increases the risk of access control errors. Site owners should document why inheritance was broken, what unique permissions were applied, and when those permissions should be reviewed or reverted. Without this documentation, unique permissions accumulate into an unmaintainable tangle that obscures who has access to what.
👉 How to maintain SharePoint site security? Maintain SharePoint security through quarterly access reviews where site owners verify and remove unnecessary permissions, especially for external shares and broken inheritance points that accumulate over time. Enable automated monitoring using Microsoft Purview DLP alerts for suspicious activities like mass downloads or unusual deletion patterns, while keeping all patches current—particularly for on-premises servers which require manual updates within days of Microsoft’s security bulletins. Combine technical controls (MFA enforcement, sensitivity labels, conditional access policies) with regular user training on recognizing phishing attempts and proper sharing practices, since most breaches exploit human error rather than technical vulnerabilities.
End users
Every SharePoint user impacts security through their daily actions. Users who understand and follow security practices prevent most incidents before they occur. Those who bypass controls for convenience or through ignorance create vulnerabilities that technical measures cannot fully address.
Document classification represents a critical user responsibility. When uploading files, users must apply appropriate metadata, content types, and sensitivity labels that trigger automated protection policies. A financial report marked as “Public” might bypass DLP controls designed to prevent financial data exposure. Conversely, routine meeting notes labeled as “Confidential” create unnecessary access restrictions that impede collaboration.
Sharing decisions carry significant security implications. Users must understand the difference between sharing options: “Anyone with the link” creates essentially public access, “People in your organization” limits access to internal users, while “Specific people” provides the most control. Each sharing action should consider the content sensitivity, recipient trustworthiness, and time limitations. The July 2025 retirement of one-time passcode links forces users to be more deliberate about external sharing through proper guest accounts.
Security awareness extends to recognizing and reporting threats. Users represent both the primary target and best defense against phishing attacks. Those who verify unexpected sharing notifications, question unusual permission requests, and report suspicious activities prevent breaches that technology alone cannot stop. A user who notices their account accessing files they didn’t open might detect a compromise that automated systems missed.
Practical collaboration scenarios
Consider how these roles interact in practice.
A pharmaceutical company launches a new drug development project requiring collaboration between internal researchers, external clinical partners, and regulatory consultants. The administrator establishes baseline policies: all project sites require MFA, external sharing expires after 90 days, and documents containing patient data trigger DLP alerts.
The project site owner creates distinct libraries for different content types: research data limited to internal teams, protocol documents shared with clinical partners, and regulatory submissions accessible to consultants. They establish groups for each audience, configure appropriate permissions, and document the access model for future reference.
Researchers uploading trial data apply metadata indicating data sensitivity and regulatory requirements. This metadata triggers retention policies ensuring data preservation for the required period while preventing premature deletion. When sharing protocols with external partners, users select “Specific people” and set expiration dates aligned with project milestones.
Monthly reviews reveal that some clinical partners no longer need access after their trial sites closed. The site owner removes these permissions, documents the change, and notifies affected users. When a researcher reports receiving a suspicious document sharing email, the security team investigates, discovers a phishing attempt, and uses the incident to reinforce security training.
This collaborative approach distributes security responsibilities while maintaining central oversight. Administrators provide tools and policies, site owners implement and monitor controls, and users make informed decisions about content handling. When any role fails, the others provide compensating controls that limit potential damage. The pharmaceutical company protects sensitive trial data not through any single security measure but through coordinated efforts across all organizational levels.
👉Where to find SharePoint security settings? SharePoint Online security settings are primarily managed through three admin centers: the SharePoint admin center (https://[tenant]-admin.sharepoint.com) for site-level permissions and sharing policies, the Microsoft Purview portal for DLP rules and sensitivity labels, and the Microsoft Entra admin center for authentication and conditional access policies. For individual sites, owners access security settings through Site Settings > Site Permissions or by clicking the settings gear and selecting “Site permissions” to manage users, groups, and sharing configurations. On-premises SharePoint administrators find security settings in Central Administration under Application Management and Security sections, while site-level permissions are managed through the same Site Settings interface as SharePoint Online.
Securing SharePoint: How to Secure a SharePoint Site: Step-by-Step
Securing a SharePoint site follows a logical progression from initial planning through ongoing maintenance. Each step builds on the previous one, creating layers of protection that work together to safeguard your data. The process takes time to implement properly, but rushing through these steps or skipping them entirely leaves gaps that attackers exploit and auditors flag. Follow this sequence for new sites and use it as a checklist when reviewing existing ones.
| # | Action | Where | Notes |
| 1 | Set org-wide sharing defaults (limit “Anyone” links) | Microsoft 365 admin → SharePoint admin → Policies → Sharing | Default link: People in your org or Specific people. Set link expiration for “Anyone”. |
| 2 | Restrict partner domains | SharePoint admin → Policies → Sharing → More external sharing settings | Use allow/deny lists. Override per site if needed. |
| 3 | Configure unmanaged devices | SharePoint admin → Policies → Unmanaged devices | Block or Limited (web-only). Scope by user/group and by site. |
| 4 | Enable sensitivity label support (incl. PDFs) | Purview portal → Information protection → Labels (and SharePoint admin tenant settings) | Keeps encrypted Office/PDF searchable and governable. |
| 5 | Turn on malware detonation for files | Defender portal → Policies & rules → Threat policies → Safe Attachments | Apply to SharePoint, OneDrive, and Teams. |
| 6 | Plan for OTP link retirement | Message to users; Update help docs | Legacy OTP links don’t work after Jul 1, 2025. Re-share via Entra B2B guests. |
Step 1: Classify the site
Begin by determining what type of data your site will contain and who needs access. Assign clear categories: public information that anyone can view, internal content restricted to employees, or confidential data requiring strict controls. This classification drives all subsequent security decisions.
Apply appropriate sensitivity labels and configure the site’s privacy settings accordingly. Set sites containing sensitive data as Private, which prevents them from appearing in search results and requires explicit permission grants. For highly sensitive content, consider creating separate site collections with isolated permissions that never inherit from parent sites.
Step 2: Set up groups and roles
Create security groups before adding content or users. Establish standard groups aligned with common access patterns: Owners who manage permissions, Members who contribute content, and Visitors who only read. For complex projects, add specialized groups like External Reviewers or Financial Approvers with custom permission levels.
Use Microsoft Entra ID security groups for enterprise-wide roles that span multiple sites. These centralized groups simplify administration when employees change departments or leave the organization. Connect these groups to your SharePoint groups rather than granting direct permissions, maintaining flexibility for site-specific adjustments.
Step 3: Restrict sharing
Configure sharing settings at both tenant and site levels to prevent accidental exposure. Disable “Anyone with the link” sharing for sensitive sites, even if it’s permitted globally. Set maximum expiration periods for guest links, typically 30-90 days depending on project duration. Require owner approval for extending access beyond initial expiration dates.
Following the July 1, 2025 retirement of one-time passcode links, ensure all external sharing uses Entra ID B2B guest accounts. This change provides better auditing and control over external access. Configure guest accounts with limited permissions: view-only access by default, disabled download capabilities on unmanaged devices, and mandatory reauthentication for sensitive operations.
Step 4: Define inheritance scope
Design your information architecture to minimize inheritance breaks. Place content requiring different permissions in separate libraries rather than breaking inheritance at the folder or item level. When you must break inheritance, document the business justification, affected content, and review schedule.
| Scenario | Break inheritance? | Recommended approach |
| Different department needs access | No | Create separate library |
| Temporary project folder | No | Use expiring guest access |
| Confidential subset of documents | Maybe | Consider separate site collection |
| Single sensitive document | Rarely | Move to restricted library |
| Archive with unique retention | Yes | Document business justification |
Each broken inheritance point requires ongoing maintenance. A project site might legitimately break inheritance for a confidential budget folder, but fifty unique permissions across various documents indicates architectural problems. Restructure such sites by creating dedicated libraries for sensitive content rather than managing item-level permissions.
Step 5: Enable versioning and checkout control
Configure version history to balance storage costs with recovery needs. Most sites function well with 10-50 major versions retained. For frequently edited documents, enable minor versions during drafting but limit retention to 5-10 versions to prevent storage bloat. Critical documents like contracts or compliance records might require unlimited version retention.
Implement checkout requirements for important libraries to prevent editing conflicts and maintain clear change attribution. Mandatory checkout ensures only one person edits a document at a time, while the checkout history shows who made specific changes. For approval-driven content, enable content approval workflows that route documents through defined review stages.
| # | Action | Where | Notes / example |
| 1 | Choose a private team site and set small Owners group | Create site in SharePoint; review Members/Visitors | Keep Owners 2–5. Most users should be Members. |
| 2 | Lock down external sharing and default link | SharePoint admin → Active sites → <site> → Sharing | Pick Existing guests only or New and existing guests. Default link = Specific people. |
| 3 | Enforce unmanaged-device limits at site | SharePoint admin → Active sites → <site> → Policies → Unmanaged devices | Set Limited, web-only or read-only for unmanaged devices. |
| 4 | Block downloads where needed | Site → Share settings; or admin site policy | Use “Block download” on links or site policy for sensitive areas. |
| 5 | Set a default sensitivity label on main library | Site → Document library → Settings → Default sensitivity labels | Auto-applies to new files; guides users. |
| 6 | Extend permissions on download/copy/move | Library → Settings → Information protection | Files keep site permissions after leaving SharePoint. |
| 7 | Verify label support is on (tenant) | PowerShell or admin setting | Example: check (Get-SPOTenant).EnableSensitivityLabelforPDF. |
| 8 | Shorten Anyone-link expiration (if allowed) | SharePoint admin → Active sites → <site> → Sharing | Use a shorter duration than tenant default. |
| 9 | Limit partners by domain (optional) | SharePoint admin → Active sites → <site> → Policies → External collaboration settings | Apply site-level allowlist. |
| 10 | Apply DLP to the site | Purview portal → Data loss prevention → Policies | Start in audit; then warn/block with policy tips. |
| 11 | Run owner access reviews | SharePoint admin → Data access governance → Reports → Start site access review | Owners fix oversharing; track completion. |
| 12 | Lock down evidence handling | Purview → Roles & scopes; Activity/Content explorer | Use “Data Classification Content Download” role for evidence. |
| 13 | Replace classic Alerts | Site → Automate → Power Automate; or Rules | Alerts are retiring. Use flows or rules for notifications. |
Step 6: Apply metadata and sensitivity labels
Establish required metadata fields that support both organization and security. A simple schema might include Department, Project, Confidentiality Level, and Retention Period. Required metadata ensures consistent classification while enabling automated policies based on content attributes.
Configure sensitivity labels that automatically apply protection based on content classification. Financial documents might receive labels that encrypt content and restrict access to finance team members. Marketing materials could get labels allowing broader sharing but preventing external downloads. Apply default labels at the library level to ensure new documents receive appropriate protection immediately upon upload.
Step 7: Strengthen authentication
Enable multi-factor authentication for all users accessing the site, with no exceptions for executives or service accounts. Configure conditional access policies that evaluate risk factors before granting access. Block legacy authentication protocols that bypass modern security controls.
Implement location-based restrictions for sensitive sites, blocking access from countries where you don’t operate or from anonymous proxy services. Require compliant devices for accessing confidential data, ensuring that only managed, patched, and encrypted devices can download sensitive files. For highest-risk content, require privileged access workstations or virtual desktop infrastructure that prevents data from ever residing on endpoint devices.
Step 8: Monitoring and alerting
Enable comprehensive auditing for all site activities. Configure alerts for security-relevant events: mass downloads indicating potential data theft, bulk deletions suggesting ransomware activity, or permission changes affecting sensitive content. Use Microsoft Purview DLP alerts rather than classic SharePoint alerts, which are retiring by July 2026.
Create Power Automate flows for security automation. A flow might notify administrators when external users access specific libraries, log permission changes to a centralized list for review, or automatically revoke access after project completion dates. These automations ensure consistent security responses without manual intervention.
| Check | How to test | Pass condition |
| Sharing scope | Invite a test guest; try broad links | Guest sees only what’s shared; default link is Specific people. |
| Unmanaged devices | Open site from a non-compliant browser/device | Web-only view; downloads blocked as configured. |
| Labels & egress | Create a new file; download from sensitive library | File auto-labels; downloaded file keeps site permissions (if enabled). |
| DLP | Upload a test file with dummy sensitive data | Policy tip or incident triggers as designed. |
| Access review | Start a review and assign to owners | Owners receive tasks and complete remediation. |
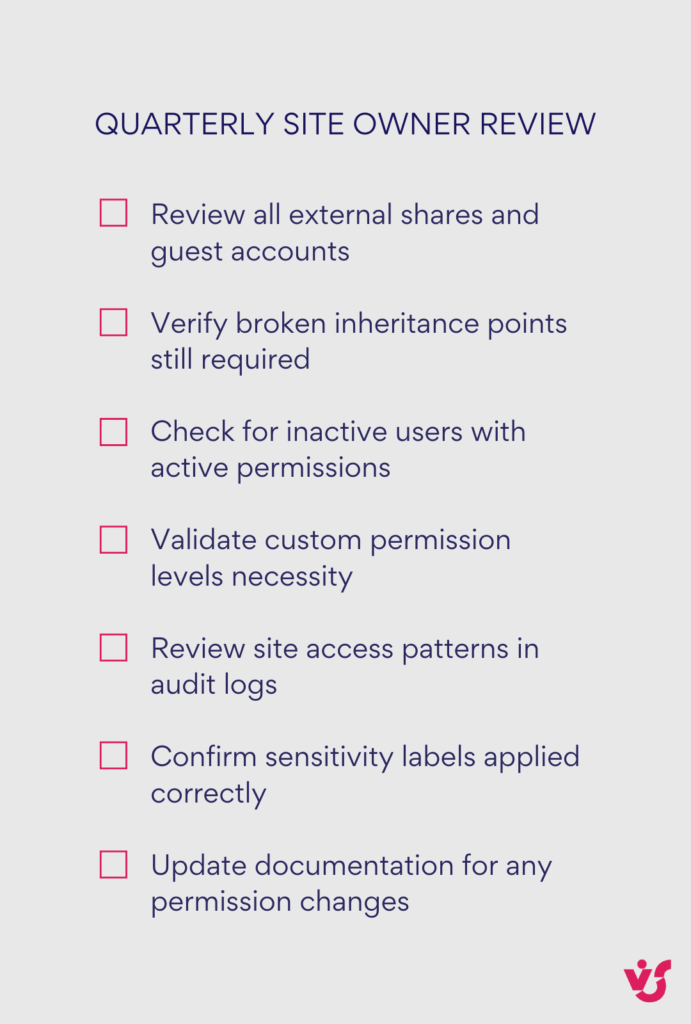
Step 9: Regular access reviews
Schedule quarterly permission reviews led by site owners. SharePoint Advanced Management’s site access reviews automate much of this process, identifying overshared content and generating specific remediation tasks. Focus reviews on external shares, broken inheritance points, and users with elevated privileges.
Conduct annual comprehensive audits examining the entire permission structure. Verify that security groups still align with organizational structure, custom permission levels remain necessary, and service accounts have appropriate restrictions. Document findings and track remediation progress to demonstrate security posture improvement over time.
Step 10: Documentation and training
Create clear documentation describing your site’s security model. Include a permission matrix showing which groups can access which content, decision criteria for breaking inheritance or granting external access, and escalation procedures for security incidents. This documentation proves invaluable during audits, troubleshooting, and knowledge transfer.
Train site owners on security responsibilities through hands-on workshops rather than abstract policy reviews. Show them how to review permissions, respond to access requests, and identify suspicious activities. Provide quick reference guides for common tasks like adding guest users or configuring library permissions. Regular refresher training ensures security knowledge remains current as SharePoint capabilities evolve.
| Action | How | Notes |
| Patch for 2025 CVEs | Apply latest SharePoint Server updates on all servers | Addresses in-the-wild exploits reported mid-2025. |
| Enable AMSI + Defender | Turn on AMSI (Full Mode) and run Microsoft Defender AV on web/app servers | Blocks malicious HTTP input and scripts. |
| Rotate machine keys | Run Machine Key Rotation job or PowerShell; recycle IIS | Prevents token replay; enforce across farm. |
| Reduce internet exposure | Remove direct internet publishing until fully remediated | Use reverse proxy/VPN; least-exposed design. |
VirtoSoftware Specialized Solutions for Secure Work with SharePoint
SharePoint’s architecture supports extension through third-party applications and web parts, allowing organizations to add specialized functionality while maintaining security standards. However, these extensions must operate within Microsoft’s security framework, respecting existing permissions, roles, and data protection policies. Solutions that bypass built-in controls or create parallel security systems introduce vulnerabilities that compromise the entire platform.
VirtoSoftware tools follow Microsoft’s security architecture principles, functioning as native SharePoint components rather than external applications. They enhance SharePoint’s capabilities while respecting all existing security configurations, ensuring that organizations can add functionality without sacrificing the protection they’ve carefully implemented.
Three key security aspects of VirtoSoftware solutions
First, all VirtoSoftware products operate entirely within the Microsoft security architecture. They use SharePoint’s standard permission system, meaning that if a user lacks access to a document library, they cannot access it through a VirtoSoftware tool either. The solutions respect role-based access controls, honor scope limitations, and work through SharePoint’s authentication mechanisms rather than implementing separate security layers.
Second, VirtoSoftware solutions maintain full compliance with Microsoft 365 and SharePoint security policies. They introduce no additional attack surfaces or vulnerabilities beyond what exists in native SharePoint. Existing Data Loss Prevention policies, compliance rules, and audit mechanisms continue functioning normally. Organizations can deploy VirtoSoftware tools without modifying security configurations or creating policy exceptions. The solutions integrate with SharePoint’s infrastructure rather than requiring separate servers, databases, or authentication systems that would expand the security perimeter.
Third, these tools meet the stringent requirements of highly regulated industries. Healthcare organizations subject to HIPAA compliance can use VirtoSoftware solutions for managing patient scheduling and clinical workflows, knowing that all data remains within SharePoint’s encrypted, audited environment. Educational institutions protect student records while enabling collaborative learning platforms. Government agencies operating in classified or isolated networks can deploy VirtoSoftware tools without introducing external dependencies or cloud connections that violate security protocols.
VirtoSoftware solutions for SharePoint Online
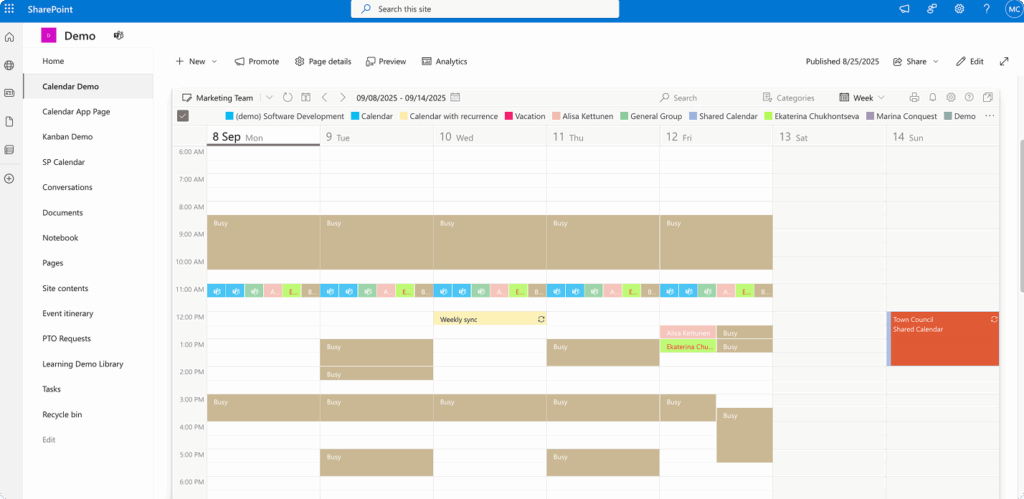
Virto Calendar App provides secure calendar management directly within Microsoft Teams and SharePoint. The solution consolidates events from SharePoint, Exchange, Google, and more into one calendar view for simplified planning while maintaining full integration with M365, providing consistency in security and UX. Organizations can overlay multiple calendars with color-coding for better visibility while all permissions flow through SharePoint’s existing security model.
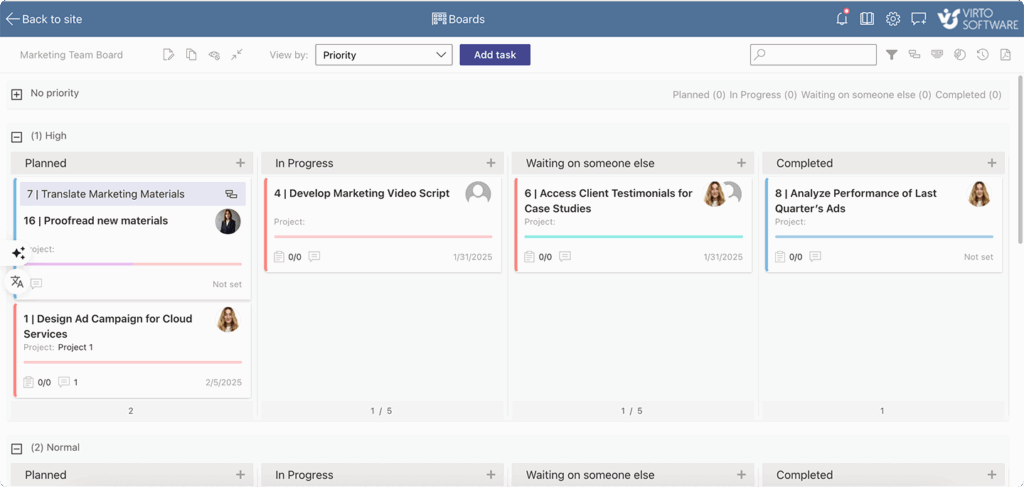
Virto Kanban Board App brings visual task management to Teams and SharePoint Online. The app seamlessly displays Kanban boards on Microsoft Teams channel tabs or SharePoint Sites, eliminating the need for constant context switching and simplifying project management. When users interact with tasks on their Kanban Board, they work with data that fetches content from SharePoint sites with bi-directional interactivity, ensuring all SharePoint permissions remain enforced. The board respects existing access groups and roles, ensuring task information remains visible only to authorized users.
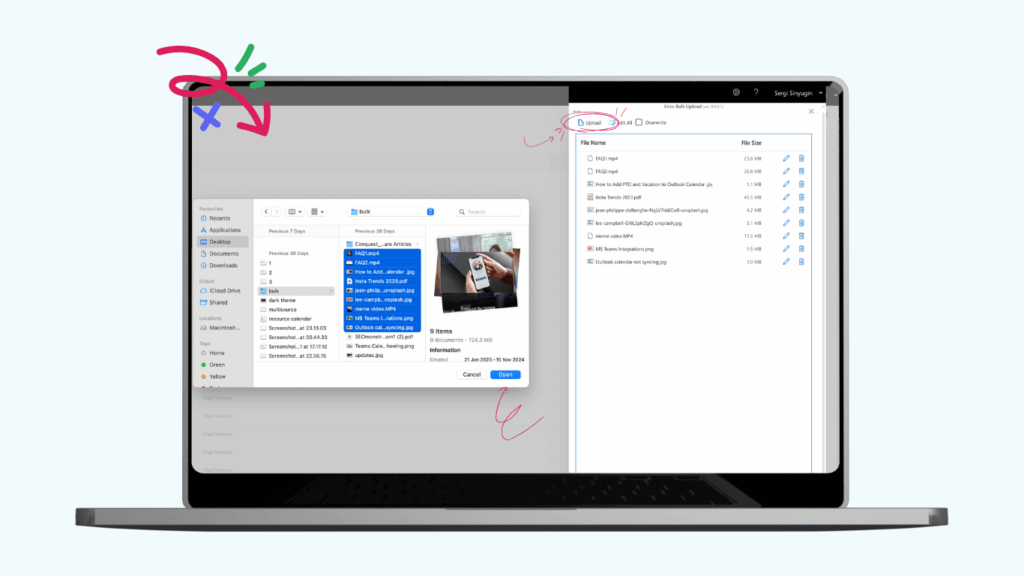
Virto Multiple File Upload App enables bulk file operations while maintaining SharePoint’s security policies. Organizations can upload hundreds or thousands of files to SharePoint libraries efficiently, with each operation respecting existing permissions, metadata requirements, and DLP policies. The tool proves invaluable during migrations, document archiving projects, or when processing large volumes of regulated content that must maintain audit trails.
VirtoSoftware tools for SharePoint On-Premise
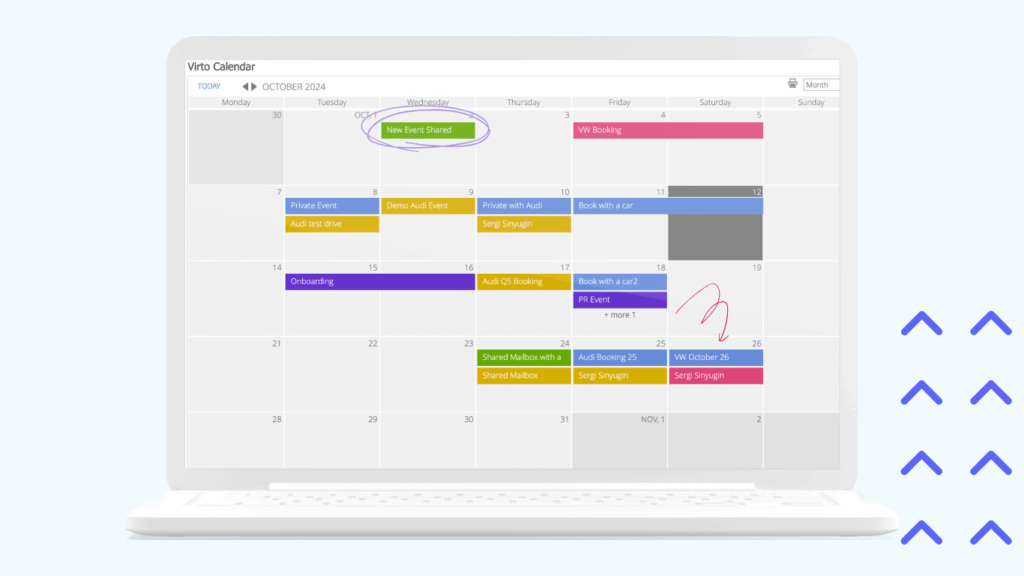
Virto Calendar Web Part delivers enterprise calendar functionality within on-premises environments. The solution works entirely within the existing SharePoint security model, making it suitable for government agencies and defense contractors operating in air-gapped networks. It provides the same overlay and color-coding capabilities as the online version while respecting all on-premises authentication and authorization configurations.
Virto Kanban Board Web Part offers project and task management with flexible access rights control tailored for closed corporate infrastructures. Organizations with strict data residency requirements can implement visual workflow management without cloud dependencies. The web part integrates with existing SharePoint task lists, maintaining all permission inheritance and security trimming that administrators have configured.
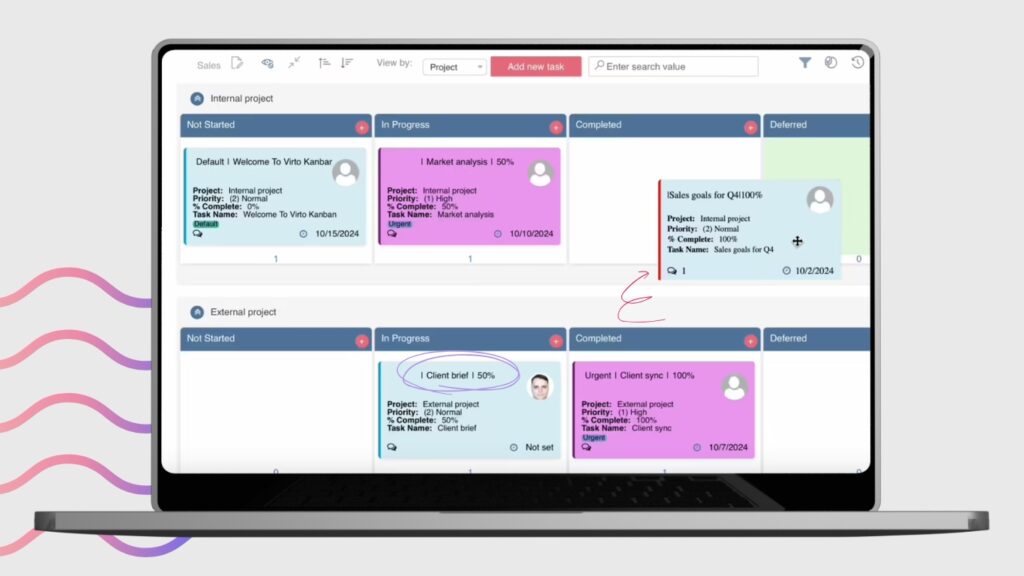
Virto Gantt Chart Web Part enables secure project planning and timeline visualization in on-premises deployments. Project managers can track dependencies, allocate resources, and monitor progress while all data remains within the organization’s security perimeter. The tool respects SharePoint’s permission model at every level, from viewing project overviews to editing individual task assignments.
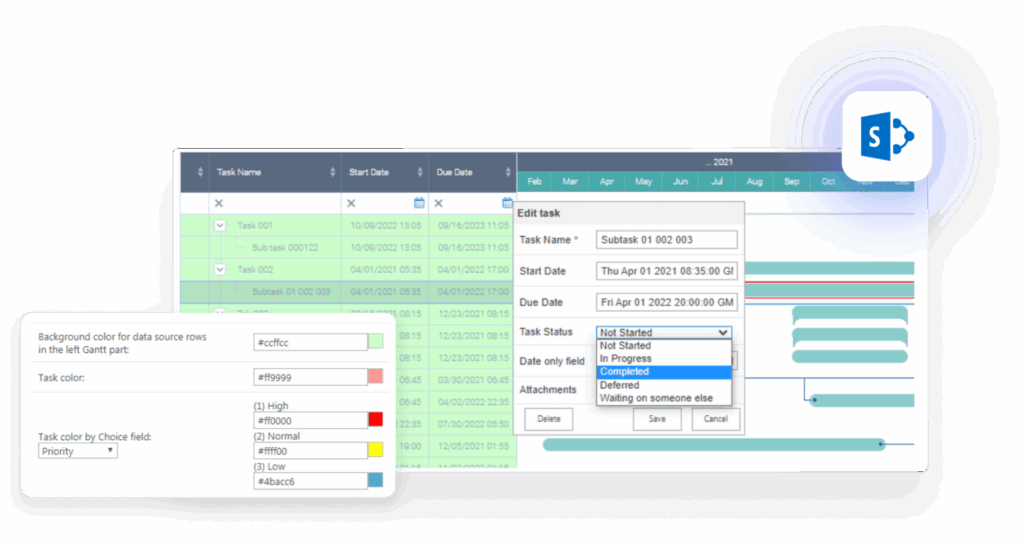
Virto Multiple File Operations provides batch file management capabilities including copy, move, and delete operations within secure SharePoint libraries. The solution performs all operations through SharePoint’s API, ensuring that security policies, audit logging, and retention rules apply to every file transaction. Organizations use it for large-scale content reorganization, archival processes, and compliance-driven file management without bypassing security controls.
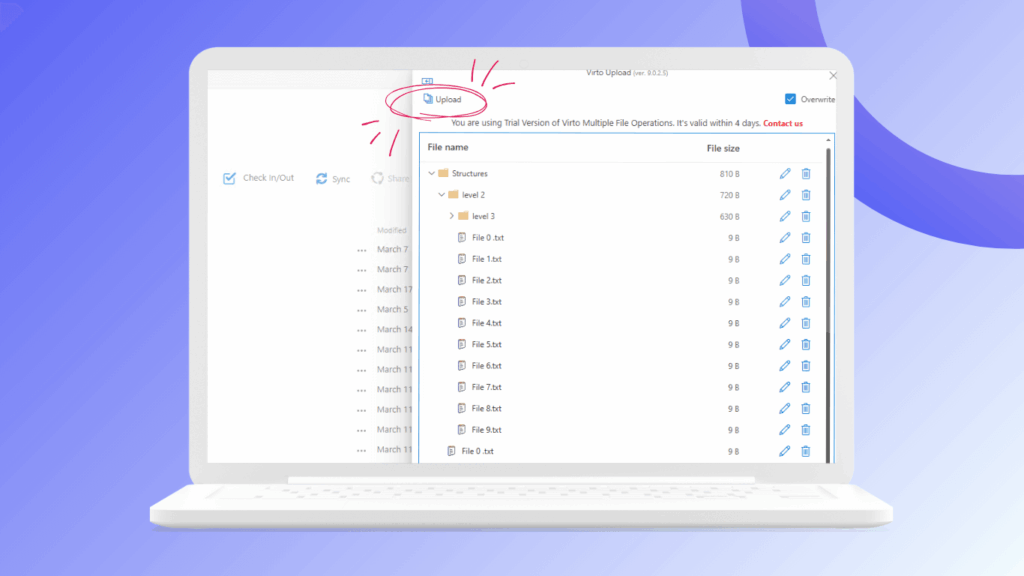
Each VirtoSoftware solution undergoes regular security updates aligned with Microsoft’s release cycles. Virto emphasizes that data security is of utmost importance, employing robust security measures in compliance with industry standards. The company provides dedicated support teams familiar with both SharePoint security requirements and industry-specific compliance needs, ensuring organizations can implement productivity enhancements while maintaining their security posture.
Conclusion on Security SharePoint
SharePoint security requires more than default settings and good intentions. It demands careful planning, consistent implementation, and ongoing vigilance. The platform provides robust security capabilities, from granular permissions and encryption to comprehensive auditing and automated policies. Yet these features only protect your data when properly configured and actively maintained.
The recent vulnerabilities exploited in SharePoint Server deployments serve as a stark reminder that security is an ongoing responsibility, not a one-time configuration. Organizations must stay current with patches, regularly audit permissions, and adapt their security posture as threats evolve. Whether you operate in the cloud with SharePoint Online or maintain on-premises servers, the fundamental principles remain constant: apply least privilege access, enable multi-factor authentication, monitor suspicious activities, and train users to recognize threats.
Success in SharePoint security comes from balancing protection with productivity. Overly restrictive policies frustrate users and encourage workarounds that create greater risks. Insufficient controls expose sensitive data to breach or loss. The organizations that achieve this balance understand that security involves everyone: administrators who configure and monitor systems, site owners who manage permissions responsibly, and users who handle data appropriately.
As your SharePoint environment grows and evolves, consider how specialized tools can enhance both security and functionality. VirtoSoftware solutions demonstrate that organizations don’t need to sacrifice productivity for protection. By working within SharePoint’s security framework rather than around it, these tools add capabilities while maintaining the security standards you’ve established.
Explore how VirtoSoftware solutions can enhance your SharePoint environment without compromising data protection. Schedule a personalized demo to see how Virto Calendar, Virto Kanban Board, and other tools work within your specific security requirements. Our team will demonstrate how these solutions respect your existing permissions, comply with your industry regulations, and integrate with your current SharePoint configuration.
Prefer to evaluate the tools yourself? Start a free 14-day trial directly from the VirtoSoftware website. Install the apps in your SharePoint Online or On-Premise environment and experience firsthand how they enhance functionality while maintaining full compliance with Microsoft’s security architecture
In the meantime, explore additional resources:
Official Microsoft resources:
- Cloud data security measures in SharePoint & OneDrive
- Disrupting active exploitation of on-premises SharePoint vulnerabilities | Microsoft Security Blog
- Managing SharePoint Online Security: A Team Effort | Microsoft Learn
- Security and Compliance | Microsoft Learn
Our blog:
- VirtoSoftware Blog: Learn about Sharepoint Online
- SharePoint Document Library: Best Practices and Examples
- SharePoint Overview: Your Ultimate Guide to Collaboration and Document Management
- Best Practices for SharePoint Document Management, Library, Folder Structure and Security
- SharePoint vs OneDrive: Features, Differences, and Use Cases
- SharePoint Classic vs Modern: A Comprehensive Comparison
- SharePoint Hub Site: Features, Benefits, and Best Practices
- SharePoint Copilot: AI Tools for Smarter Collaboration
- Types of SharePoint Sites: Features, Uses & Selection Guide
- SharePoint Pages: What They Are, How to Create and Optimize