With over 200 million active users and adoption by 80% of Fortune 500 companies, SharePoint has emerged as the content collaboration powerhouse for global enterprises. Commanding 75% market share in its category, SharePoint manages mission-critical information for leading organizations worldwide (1).
What explains SharePoint’s meteoric rise is its unparalleled versatility, security and scalability, which enable deployments supporting thousands of users just as readily as small workgroups. Whether building company-wide knowledge management portals or streamlining document sharing for a department, SharePoint’s robust feature set adapts to countless collaboration scenarios.
But as a business using SharePoint, you’re still faced with the challenge of determining and setting the proper permissions to secure your data and content. In the context of SharePoint, permission refers to the level of access or authority granted to a user or group of users to perform specific actions or view specific content within a SharePoint site, list or library.
While this may seem like a straightforward process, we all know that getting it wrong can lead to serious security and usability issues. That’s why it’s essential to understand the best practices for setting up permissions and get it done right the first time.
This article aims to provide a comprehensive guide to best practices for managing and setting up SharePoint permissions, covering everything from setting up permission levels to managing permissions for data, documents, sites, lists, and libraries.
At VirtoSoftware, we are here to help. As a SharePoint component development specialist, we advise clients on how to set up and operate SharePoint permissions on a daily basis with expertise you can trust.
However, please keep in mind that this article provides an overview of the topic, and we recommend consulting the official Microsoft documentation on this topic, which includes the following resources:
- User permissions and permission levels
- Customize permissions for a SharePoint list or library
- Overview of site permissions in SharePoint Server
What are the Different Permissions in SharePoint: Understanding SharePoint Permissions
The SharePoint platform offers a variety of permission levels that govern access to content and data, but the landscape can quickly become complex. Here we’ll cover the first set of concepts related to information security across the platform, starting with the main types of SharePoint permissions you’ll encounter.
- User permissions: This is the most granular level of permissions, targeting individual user accounts. User permissions can be explicitly assigned, although it’s recommended to use group permissions for easier management. Features include the ability to view, edit, or manage content, creating a tailored experience for each user based on what they need to accomplish.
- Read: Users can view items and download documents.
- Contribute: Users can add, edit, and delete items in existing lists and document libraries.
- Full Control: Users have complete access to all settings and features.
Purpose: To provide or restrict access to specific individuals, often reflecting their roles within the organization.
- Group permissions: Groups are collections of users that can be managed as a single entity. SharePoint permissions groups come with predefined permission sets, though custom groups can be created to match organizational needs.
- Visitors: Typically have ‘Read’ permissions.
- Members: Commonly have ‘Contribute’ permissions.
- Owners: Usually have ‘Full Control’ permissions.
Purpose: To streamline permission management by collectively administering access rights to users who require similar access levels, reducing the complexity associated with individual user management.
- List/Library-Level permissions: These permissions are applied to specific lists or document libraries, rather than the entire site.
- Design: Users can view, add, update, delete, approve, and customize.
- Edit: Users can add, edit, and delete lists; can view, add, update, and delete list items and documents.
Purpose: To provide access control over specific content areas within SharePoint. This focus ensures that sensitive information stays protected, and only relevant users can manipulate the content.
It’s important to tailor the use of these permissions carefully, considering both organizational requirements and the overarching principle of least privilege, where users are granted the minimum levels of access—or permissions—needed to perform their jobs. Well-structured permissions facilitate a secure and efficient environment, fostering productivity without compromising security.
👉 Sharepoint permissions edit vs contribute—what’s the difference? In SharePoint, the permissions levels of “Edit” and “Contribute” provide users with different levels of access to sites, lists, and libraries. The “Contribute” permission level is typically used to give users the ability to view, add, update, and delete items in lists and libraries. The Contribute level does not allow users to change library and list settings, nor does it allow them to manage permissions or site settings. The “Edit” permission level, on the other hand, includes all the permissions found in Contribute, but it also allows users to manage lists. The additional rights provided by the Edit permission level can have significant impacts, especially if lists are central to the site’s operation. Edit permissions are typically granted to users who are trusted to structure the content within a site properly, such as team leaders or project managers.
Permission levels and their impact on access to content
SharePoint permission levels are pivotal in delineating what users can and cannot do within the SharePoint environment, and managing them effectively is crucial to operational security.
Here’s an overview of some common permission levels discussed above and their impact on access to content:
- Read: Users with ‘Read’ permission level can access content, download documents, and view list items, site pages, and other content within the site. They cannot edit or delete content, limiting their interaction to consumption of information.
- Contribute: The ‘Contribute’ permission level allows users to view, add, update, and delete items in lists and libraries. This enables collaboration on documents and data but does not allow changes to site structure or the creation of new sites.
- Edit: Users with ‘Edit’ permissions can manage lists, which means they can add, edit, and delete lists, as well as add, update, and delete list items and documents. They have more authority than the ‘Contribute’ level but still cannot alter site settings.
- Design: This level includes all the permissions of ‘Edit’, plus the ability to change site layout and design. Users can create, change, and delete site pages, and modify the structure of the site, impacting how content is displayed and organized.
- Full Control: Users with ‘Full Control’ have unrestricted access to all settings and capabilities, including the management of permissions themselves, deletion of the site, and the ability to add or remove apps. This level should be restricted to administrators and key decision-makers within the organization.
Adjusting permissions directly impacts a user’s ability to create, edit, delete and restore SharePoint content across the platform. From restricting confidential documents to specific groups to opening up team sites for broad editing access, dialing in the right roles and permissions promotes security while enabling workflow efficiency. Minor permission changes can introduce major collaboration friction if not accounting for business needs and user expectations.
Here’s an overview of how changing permission levels can impact users’ abilities:
- Reducing permission level: When a user’s permission level is decreased, they may lose the ability to edit content they were previously able to modify, which can hinder their workflow and collaboration efforts. Care must be taken to ensure essential contributors have the necessary permissions to fulfill their roles.
- Increasing permission level: Conversely, increasing a user’s permission level can facilitate their work by allowing them greater access to data and content. It’s essential to assess the need carefully, as this can inadvertently lead to compromised security if users are granted more access than required for their tasks.
- Custom permission levels: SharePoint allows the creation of custom permission levels. By tailoring permissions, administrators can ensure that users have exactly the access they need—no more, no less. However, this customization requires thorough understanding to avoid creating security holes.
In practice, configuring SharePoint permissions demands judicious trade-offs between access and security to pinpoint the sweet spot for your organization. As new users join or responsibilities shift, the right balances follow suit. Through ongoing visibility into how teams collaborate, IT administrators can continually reassess that the lowest necessary permission levels are applied based on current user duties. Periodic access reviews help determine that security policies align with permission schemes as projects progress and personnel change.
How to Edit Permissions in SharePoint: Explanation and Management of Permissions at the Site, List, and Library Levels in SharePoint
In this section, we’ll give detailed instructions on setting SharePoint permissions at the site, list, and library levels, as well as give practical tips on managing them.
| SharePoint roles and permissions | In SharePoint, roles and permissions are integral to the platform’s security architecture, allowing administrators to control user actions within the site. SharePoint roles typically refer to SharePoint groups, which are collections of users who have the same sets of permissions. Permissions are specific access rights that are granted to users or SharePoint groups, and they control the level of access that the user or group has to sites, lists, libraries, folders, and items. SharePoint roles and permissions work together to form a permissions hierarchy that governs access and activities within a site. |
| SharePoint site permissions | SharePoint site permissions are access rights granted at the site level and affect everything within that site, including lists, libraries, and folders (unless these have been uniquely permissioned). The default permission groups in SharePoint are Owners, Members, and Visitors, although administrators can create more groups with custom levels of access. |
| SharePoint page permissions | SharePoint page permissions refer to the permissions assigned to individual pages within a SharePoint site. Pages in SharePoint are where information is displayed and interacted with—like a team’s home page, a news post, or a dashboard with web parts. These permissions can be set to inherit from the parent site, or they can be unique if you need tighter control over who sees or edits certain pages. |
| SharePoint list permissions | SharePoint list permissions refer to the access rights assigned to users and groups specifically for a list in SharePoint. A list in SharePoint is a collection of data that can be shared with team members and typically includes columns or fields that can be used to sort, filter, or group information. These permissions can be unique to a list, or they can inherit permissions from the parent site. List-level permissions give SharePoint administrators the flexibility to control access on a more granular level than site-wide permissions. |
| SharePoint document library Permissions | SharePoint library permissions focus specifically on the access rights for a library—a special type of list in SharePoint designed to store, organize, and share documents. Like lists, libraries can have either unique permissions or inherit permissions from the parent site. |
| SharePoint folder permissions | SharePoint folder permissions apply to folders within document libraries or lists, which help organize content into a hierarchical structure. Folder permissions are managed similarly to list permissions. Like list permissions, folder permissions can be uniquely set or inherited from the parent list or document library they reside in. |
| SharePoint group permissions | SharePoint group permissions are associated with SharePoint groups, which are collections of users treated as a single entity. A group permission set simplifies permission management by allowing you to assign access rights to multiple users at once, rather than individually. SharePoint comes with default groups like ‘Owners’, ‘Members’, and ‘Visitors’, each with different permission levels. You can also create custom groups to meet specific needs, assigning them as narrow or as broad an access level as required. |
| SharePoint user permissions | SharePoint user permissions are the access rights assigned directly to individual users. Administrators can granularly control what each user can or cannot do. User permissions can be layered on top of group permissions and can be detailed down to individual items or documents for sensitive content. It’s worth noting that overuse of unique user permissions can lead to a complex and hard-to-manage permission structure, which is why grouping users and assigning group permissions is usually preferred. |
| SharePoint member permissions | In SharePoint, there are various predefined security groups with associated permission levels that define the capabilities of users within those groups. One common group is the “Members” group. This group typically has “Edit” permissions, which allows its members to add, edit, and delete lists and items within the site where they are granted those permissions. |
How to Manage Permissions at the SharePoint Site Level
At the site level, permissions determine the entire team’s ability to interact with content and collaborate within that site. When managed well, permissions enhance productivity and safeguard critical information. When managed poorly, they can be a source of both frustration and inadvertent data breaches. This section provides a practical walkthrough for administrators on managing site-level permissions, ensuring that users have the access they need without compromising the integrity and security of the site.
- Navigate to site settings:
- Access your SharePoint site.
- Click the gear icon in the top right corner to open the settings menu.
- Select ‘Site permissions’ under the ‘Users and Permissions’ category.
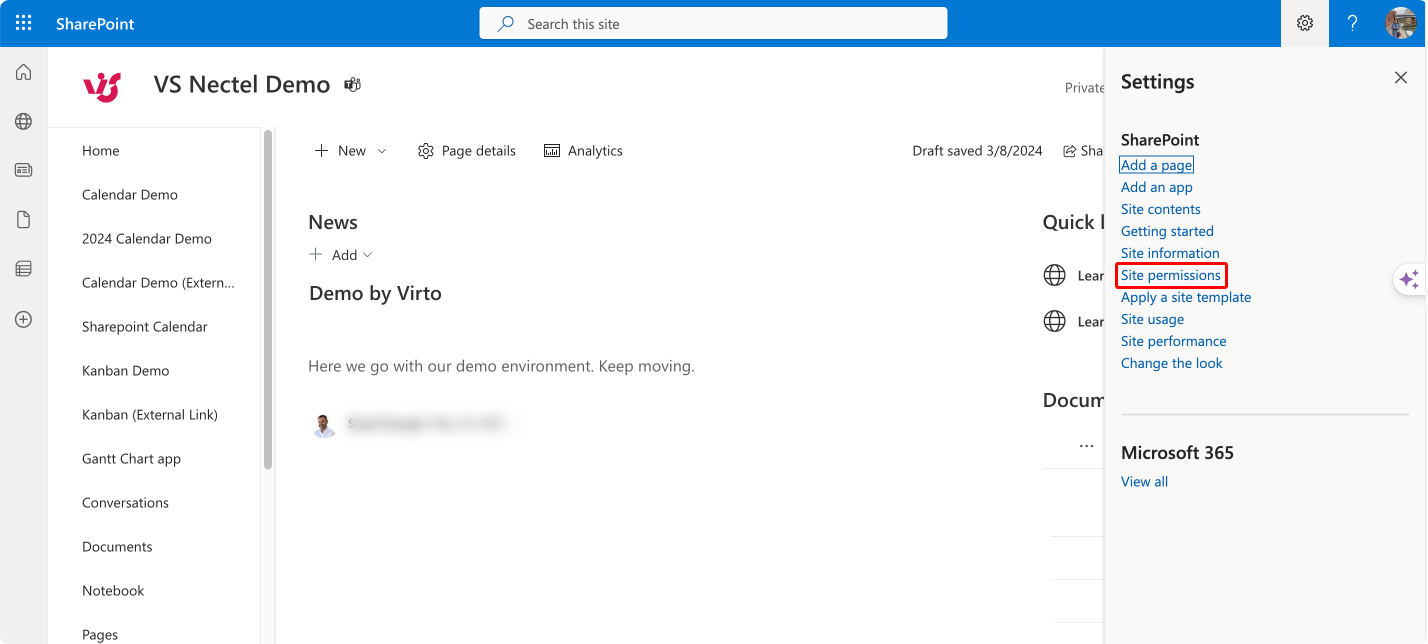
Pic.1 Selecting “Site permissions” on the SharePoint site.
- Understand the permission groups: Familiarize yourself with the default SharePoint groups—Owners, Members, and Guests—or create a new group if necessary by selecting ‘Create Group’. If you don’t see ‘Create Group,’ click on ‘Advanced permission settings’.
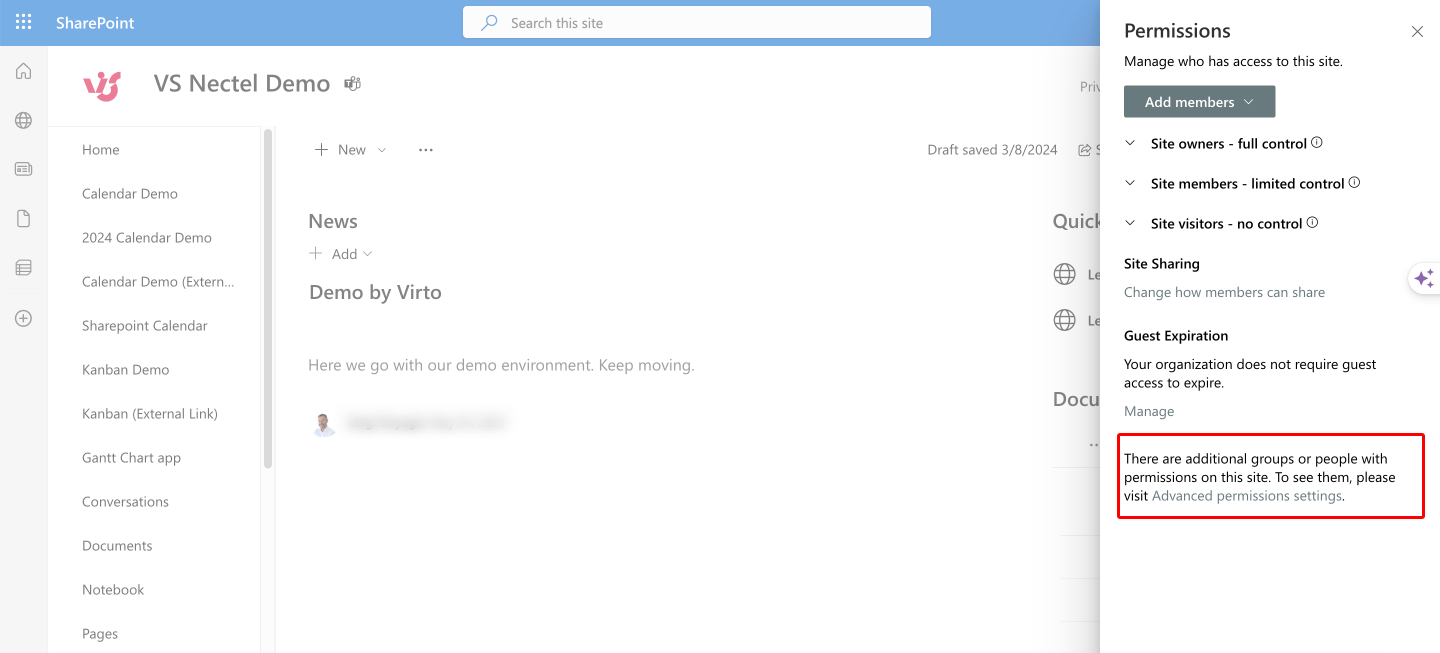
Pic. 2. Choosing “Advanced permissions settings” if you don’t see the details you’d like to edit in the default window.
- Add or remove users/groups:
- To add users to a group, select the group and click on ‘Add members’ to add users or another group to this permission level.
- To remove users or groups, select the group, choose the individual users/groups, and click ‘Remove User Permissions’.
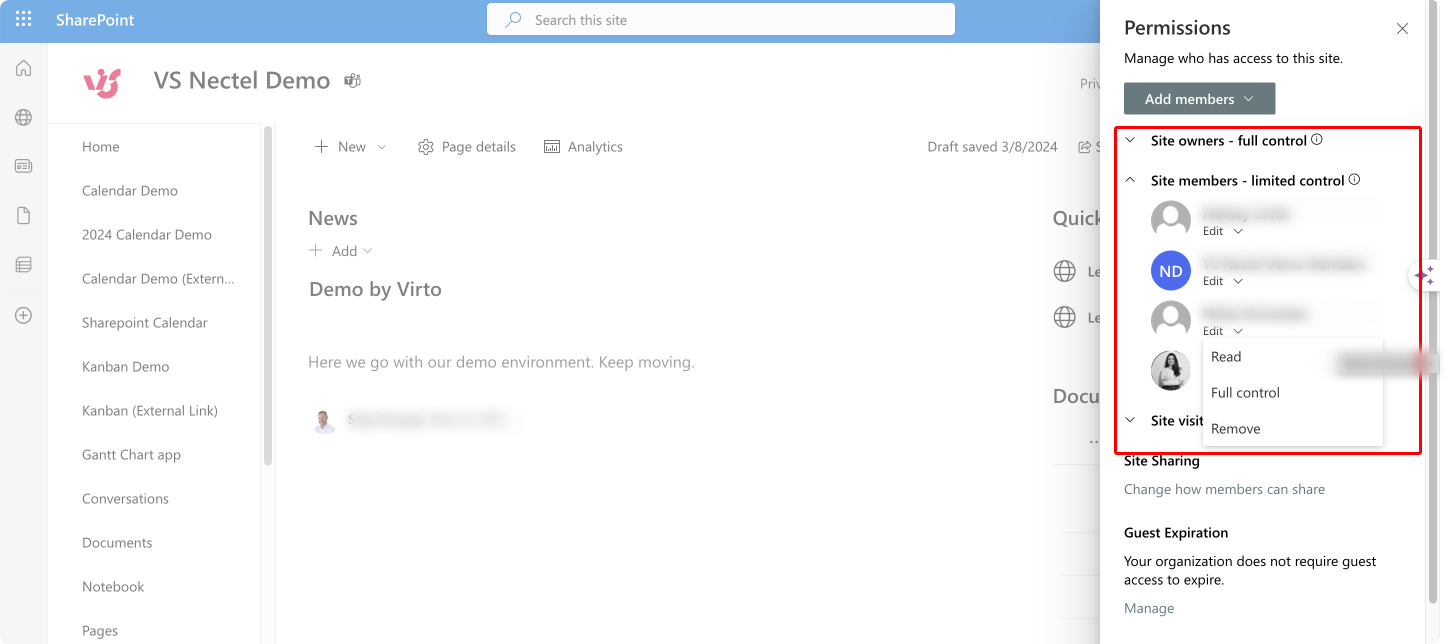
Pic. 3. Editing permissions for the SharePoint site members.
- Grant or modify permissions: Use the ‘Grant Permissions’ button to assign permissions to users or groups. Select the appropriate permission level for these users/groups.
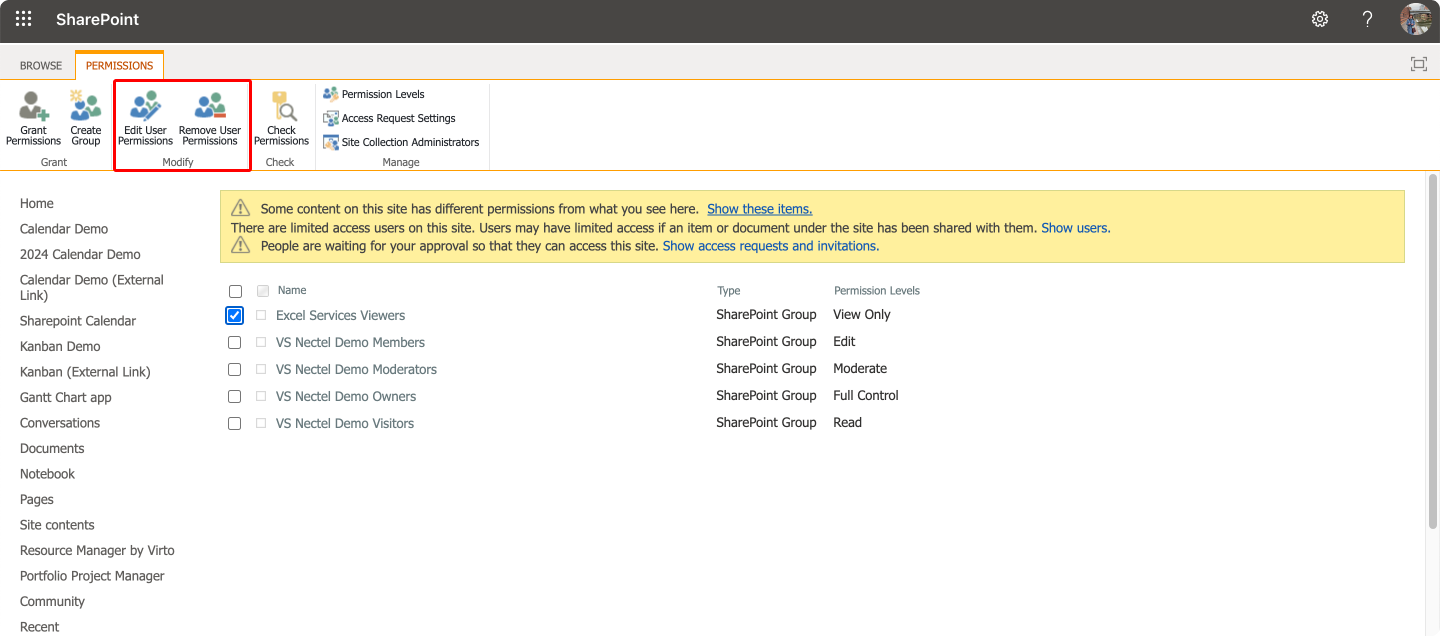
Pic. 4. Editing and removing user permissions in the “Advanced permissions settings”.
- Managing inheritance: Decide if sub-sites should inherit permissions from the parent site. By default, they do, but you can break this inheritance if a sub-site requires unique permissions by clicking ‘Stop Inheriting Permissions’.
- Monitor permissions: Regularly check and adjust permissions as necessary to ensure they match current project and organizational needs.
Use the following SharePoint features to manage site permissions efficiently:
- Permission levels: To fine-tune what users can do.
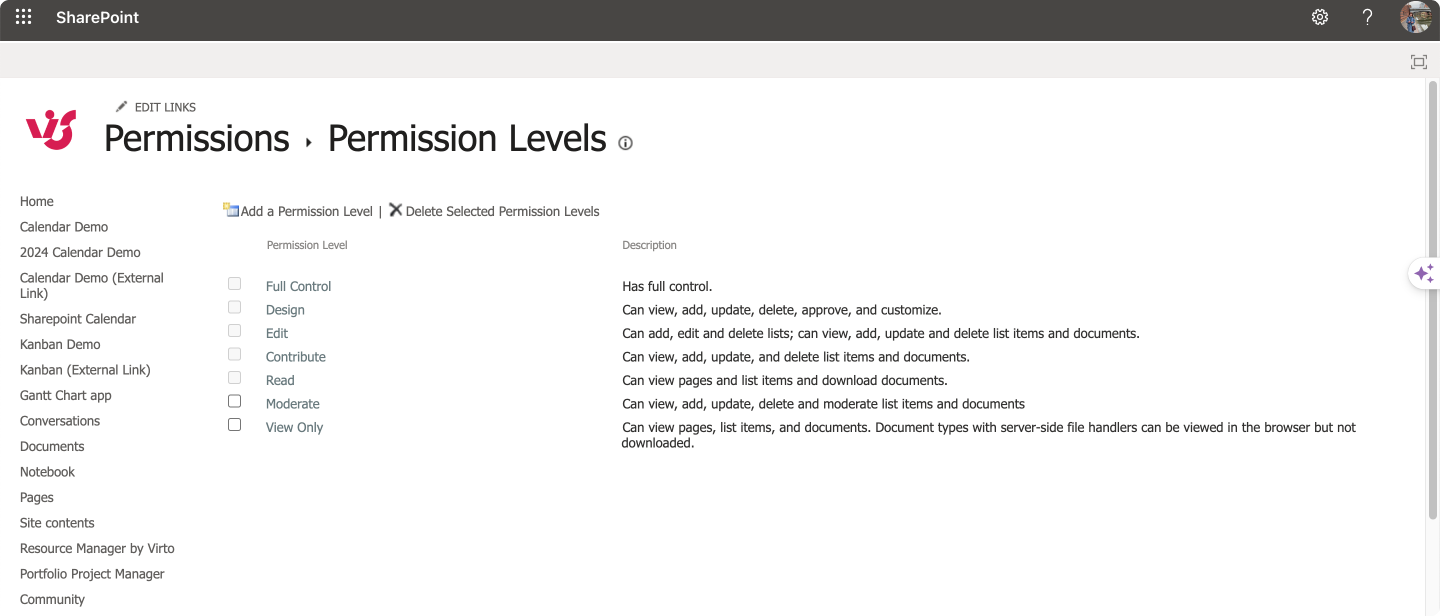
Pic. 5. Managing permission levels on the SharePoint site.
- Group management: To administer permissions for multiple users at once.
- Inheritance settings: To manage permission flow from parent to child content.
Managing permissions at the SharePoint site level is a responsibility that should be approached methodically. Remember to periodically review and update permissions as roles change within your team and as your organization evolves.
How to manage SharePoint permissions for lists and libraries
Setting permissions for lists and libraries in SharePoint is another essential task that ensures the right people have access to the right information. It allows SharePoint administrators to tightly control who can view or edit content within each list or document library, which is particularly important for sensitive or confidential information.
Here’s how you can set permissions for lists and libraries in SharePoint:
- Navigate to the list or library:
- Go to the SharePoint site containing the list or library you wish to manage.
- Click on the list or library in the Quick Launch bar, or click on ‘Site Contents’ and then on the list or library name.
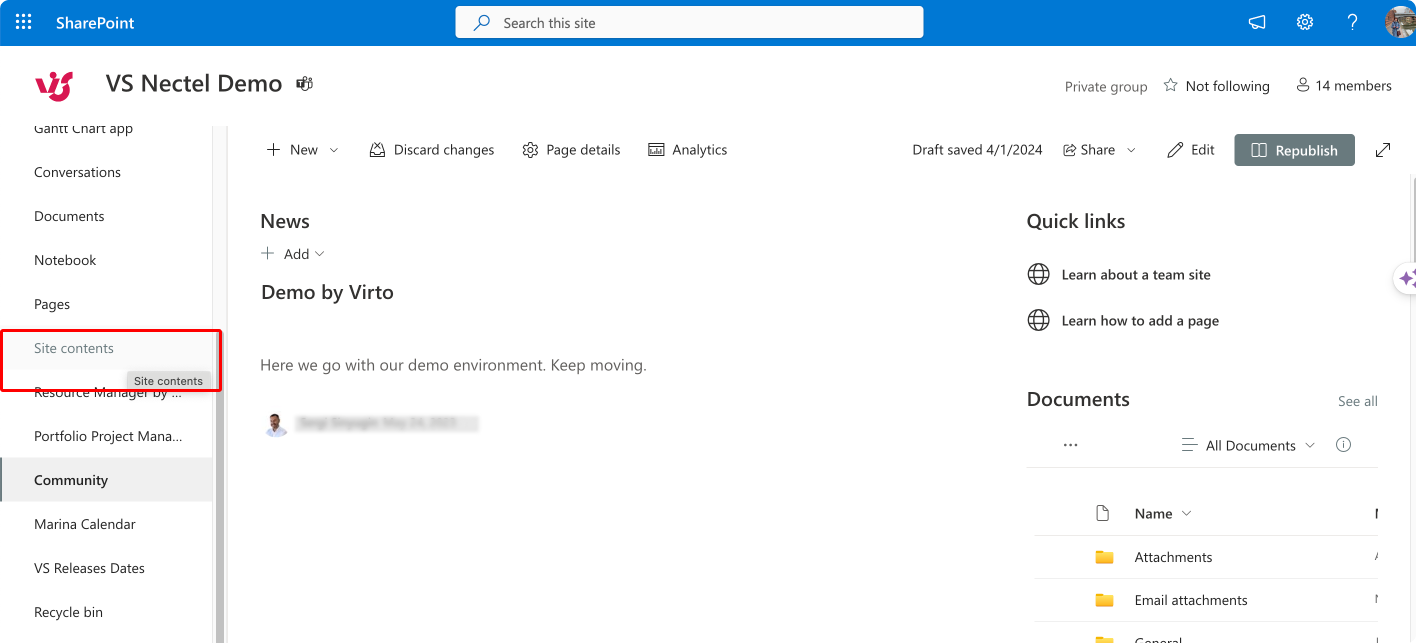
Pic. 6. Navigating to “Site contents”.
- Access the settings: Once you’re in the list or library, click on the gear icon to open the ‘Settings’, and then select either ‘Library settings’ or ‘List settings’ depending on which one you are managing.
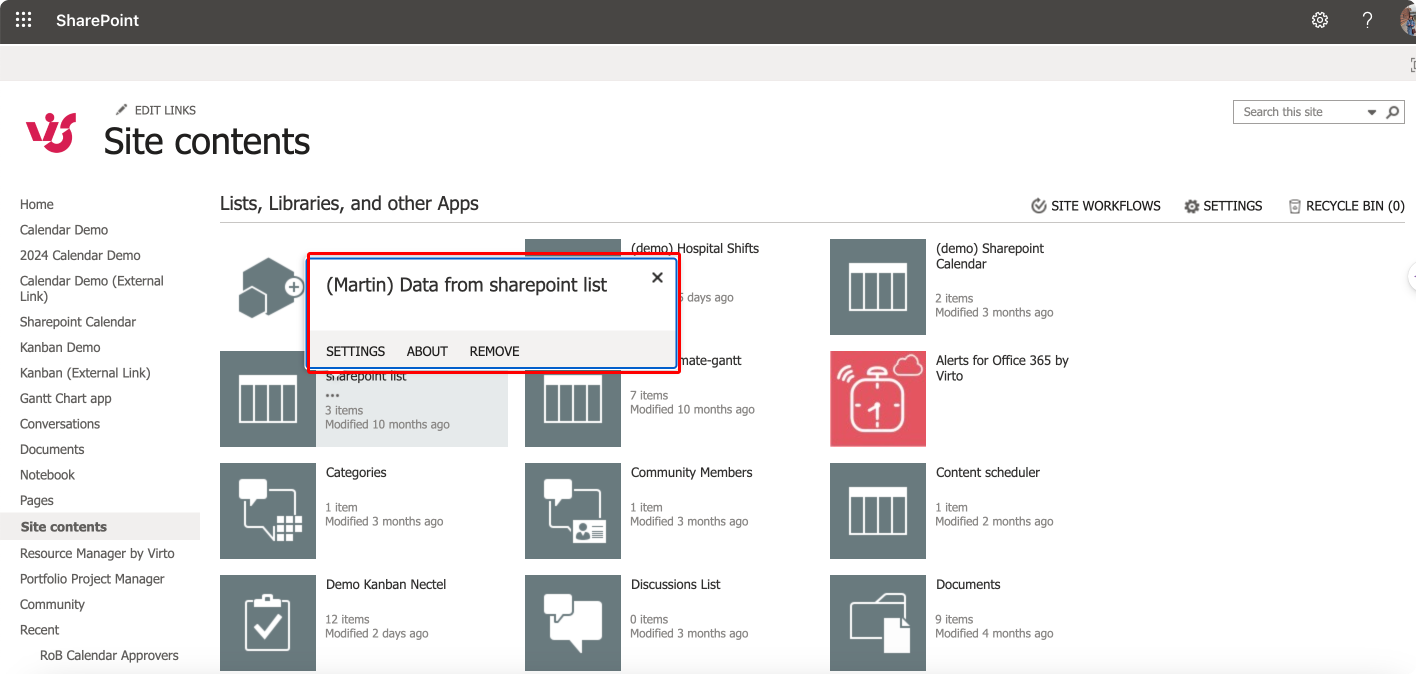
Pic. 7. Accessing settings for a list.
- Manage permissions: Under ‘Permissions and Management’, click on ‘Permissions for this library’ or ‘Permissions for this list’.
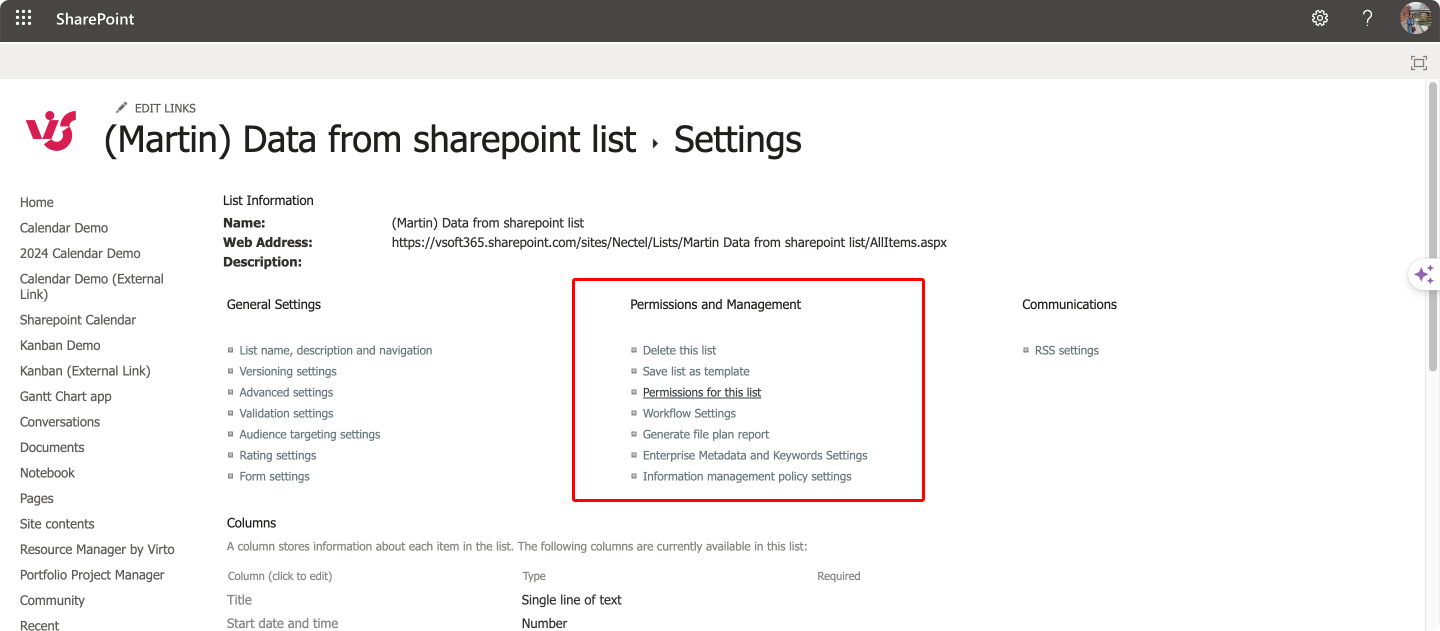
Pic. 8. Navigating to the list permissions.
Here, you will see if the list or library is inheriting permissions from the parent site. If yes, and you wish to set unique permissions, click on ‘Stop Inheriting Permissions’. You’ll be warned that this will create a unique set of permissions for the list or library independent of the parent site.
Pic. 9. Navigating to the ribbon bar with the “Managing Parent” and “Stop Inheriting Permissions” options.
- Edit permissions: Once inheritance is stopped, you can remove or change group or individual permissions as necessary. Click on ‘Grant Permissions’ to add new users or groups.
- Configure access requests: Optionally, configure access request settings by clicking on ‘Access Request Settings’ to manage how users can request access to the list or library.
As you know, list and document libraries represent common collaboration hubs where users create, share and edit files. By aligning access controls to business needs, SharePoint administrators can enable productivity while securing sensitive information. To help you configure those granular permissions and manage them even more effectively, here are a few best practices to follow:
- Always use groups rather than individual permissions for ease of management and to avoid individual-user access sprawl.
- Break inheritance sparingly. Every unique permission set increases administrative complexity and should only be used when essential.
- Use SharePoint groups and permission levels such as View, Edit, and Full Control appropriately.
- Review and clean up permissions regularly. This helps ensure that only the necessary individuals have access to sensitive information.
- If you need to set unique permissions for some items but not others, consider using permissions at the folder level within a library.
- Understand and make use of advanced permissions features like SharePoint Groups, Permission Levels, and sharing links with specific access rights in SharePoint Online.
- Implement and maintain an auditing process to monitor who has access to what.
- Train users on proper sharing protocols to avoid accidental leaks of sensitive information.
Examples of using different access levels to ensure data security
Below are real-world scenarios illustrating how different access levels can be applied within SharePoint to safeguard data while supporting various business functions and collaboration needs. These scenarios highlight the importance of understanding and judiciously applying SharePoint’s hierarchical access levels—from Full Control to Read Only—to various contexts where data protection sensitivities may vary.
Scenario: protecting confidential business documents
- Full Control: Assigned to the IT department’s SharePoint administrators. They maintain the sites and have the capability to set permissions for other users.
- Edit Access: Granted to the legal team and senior managers who need to draft, revise, and approve policy documents stored in a specific document library.
- Read Only: Given to regular employees who need to view these documents for compliance purposes but should not alter them under any circumstance.
Scenario: Managing collaborative workspaces
- Edit Access: Assigned to team members within a collaborative workspace such as a departmental site where daily operations and projects are managed. Users can add, update, or delete content as the projects evolve.
- Read Only: Provided to stakeholders or auditors who need to review the project’s progress and documents but should not intervene in the project’s operational aspects.
Scenario: Working with external partners
- Limited Access: Used when external partners or consultants require access to specific documents within a library for review or one-time input. They don’t have visibility into the rest of the site’s content, ensuring other sensitive information remains secure.
Scenario: Hosting sensitive research data
- Read Only: Applied to a research library containing sensitive data, where research analysts can access data sets but cannot modify them, preserving the integrity of the research.
- Full Control: Limited to a select few senior research administrators responsible for managing and disseminating research findings securely.
Scenario: Temporary project sites
- Edit Access: Given to project team members for the duration of a project, allowing them to manage task lists, documentations, and discussions.
- Limited Access: Granted to clients or project sponsors who may need to view certain documents or milestones within the project site but should not have wider access.
Custom access levels scenario: Managing HR records
- Custom Access Level “Add Items”: You might create a custom access level for HR assistants who need to add new employee records to the HR site but should not modify or delete existing records.
The examples demonstrate that careful assignment of access levels is essential to protect sensitive information while allowing operations to continue smoothly. Higher access levels come with greater power and responsibility and should be restricted to those who need it to perform their duties. A hierarchy of access ensures that data integrity is preserved while still allowing employees the access they require to fulfill their roles.
Situations when a user has permissions but access denied SharePoint
It is possible for a user to have permissions assigned and yet face an “Access Denied” message. This discrepancy can arise from several situations:
- Unique permissions: A sub-site, list, or library may not be inheriting permissions from its parent, and the user lacks permissions on this specific resource.
- Item-level permissions: SharePoint allows individual items to have unique permissions. If these are not set correctly, a user may be able to access the list or library but not the items within it.
- Permission levels altered: If an administrator has customized permission levels, some may not include access that appears to be granted.
- Group membership not updated: Changes to group membership can take time to propagate. Likewise, if a user is removed, they may still have access until the system updates.
- Permissions cache issues: Local permissions caching on SharePoint servers may cause outdated permissions to be enforced until the cache is refreshed.
- Security group membership refresh: When using Active Directory or Azure Active Directory groups, there may be a delay in the application of new memberships.
- Site lockdown or security policies: The site may have been locked down by a SharePoint or global administrator, which can override individual permissions.
- Content approval features: If content approval is required but not yet granted, users might see ‘Access Denied’ until the content is approved.
Encountering blunt “Access Denied” errors ranks among the most frustrating experiences for both end users and SharePoint administrators alike. Effective troubleshooting begins with methodically retracing permissions throughout the environment to uncover the source of unexpected restrictions. Check site-wide roles, group affiliations and individual document or list settings to pinpoint where changes introduced breakage. Remember—whether an incomplete policy change or accidental revocation, the solution lies in the details.
Permission Considerations By Deployment Model: Permission for SharePoint Online vs SharePoint On-Premises
At their core, permissions in both SharePoint Online and SharePoint On-Premises share foundational configurations to transform broad policies into granular access controls. However, notable differences emerge when translating concepts into deployed security architectures and their respective hosting models.
While SharePoint Online offers the convenience of being cloud-based with automated updates and inherent integration with other Microsoft 365 services, SharePoint On-Premises grants IT administrators comprehensive control, which is critical for certain bespoke and complex environments. Furthermore, there’s a contrast in data security responsibility, feature availability, and even the user interface that can alter the approach towards permissions management.
Considering these general distinctions, the specifics of what’s available or manageable can shift based on the particular version of SharePoint Online and the precise configuration of SharePoint On-Premises an organization employs. To encapsulate the key differences between SharePoint Online and SharePoint On-Premises concerning permissions management, the following summary table can serve as a quick reference guide for administrators:
| Features/Aspects | SharePoint Online | SharePoint On-Premises |
|---|---|---|
| Deployment and Management Model | Managed by Microsoft; permissions managed via admin centers | Full control over permissions; managed in-house or via PowerShell |
| Updates and Maintenance | Automated updates by Microsoft | Manual updates; requires internal resources |
| Integration with Corporate Infrastructure | Simplified integration, relies on Azure AD for modern auth | Flexible integration options; supports various auth protocols |
| Functionality and Feature Availability | Regularly updated with new features; some cloud-exclusive | Updates dependent on version; some on-prem-exclusive features |
| Data Security and Storage | Microsoft cloud with Microsoft security protocols | Data stored on organization’s infrastructure with internally managed security |
| Customization and Control | Limited customization; cloud constraints | Extensive customization and control |
| Cost and Pricing Model | Subscription-based; potentially lower upfront costs | Higher upfront costs for licenses and infrastructure |
| User Interface | Modern experience; consistent interface with O365 | Traditional experience; may differ with newer updates |
While this guide focuses on configuring permissions in SharePoint Online, the overarching practices apply to on-premises implementations as well. That means you won’t face any insurmountable difficulties in recreating the steps outlined here while configuring permissions in SharePoint On-Premise. However, key differences in native tools and features warrant referring to Microsoft’s technical documentation covering the specific SharePoint edition and version your organization leverages. Always cross-reference administrator guidance to translate the concepts covered here into tailored action plans for your on-premises or online environments.
Learn more about SharePoint Online vs SharePoint On-Premises
Key things to know about permissions in SharePoint Online
When managing permissions in SharePoint Online, there are a few more things to grasp when it comes to ensuring a robust and secure working environment. Here’s a breakdown of the essentials:
- Permissions model: SharePoint Online adopts a permissions model that’s built around the ‘Least Privilege’ security principle. Users are granted the minimum levels of access—or permissions—necessary to perform their job functions. This mitigates the risk of unauthorized access to sensitive information and helps prevent data leaks.
- Managing permissions:
- Admin centers: Permissions are managed through both the Microsoft 365 admin center and SharePoint admin portal. These admin centers are where you set up and control various permission levels, user group memberships, and guest access.
- Direct access controls: Administrators can directly assign unique permissions to sites, lists, libraries, and even single items within those lists or libraries.
- Access auditing: SharePoint Online includes features that enable admins to track who has accessed which information, providing a transparent and traceable permission landscape.
- Flexibility and customization:
- Custom permission levels: Besides out-of-the-box permission levels (Full Control, Edit, Read, etc.), SharePoint Online allows for custom permission levels tailored to specific roles and responsibilities.
- Site and item-level permissions: You can adjust permissions at both the macro (site) and micro (item) levels, granting flexibility in how you manage access within your organization.
- Microsoft 365 integration:
- Unified access control: As part of the Microsoft 365 suite, SharePoint Online benefits from integration with services like Exchange Online and Microsoft Teams, allowing for consistent permission policies across applications.
- Groups and teams: SharePoint Online is designed to work closely with Microsoft 365 groups and Microsoft Teams, with group membership directly affecting access permissions within SharePoint.
- Data Security
- Cloud storage: All data is stored in Microsoft’s cloud environment, which adheres to strict security standards.
- Compliance certifications: SharePoint Online meets several industry-standard certifications (ISO 27001, SOC 2, etc.), ensuring that data security practices are up-to-date and effective.
Within complex SharePoint deployments, even principled initial permission rollouts demand ongoing management as organizations evolve. Maintaining appropriately scoped access means continually revisiting policies through: training to establish expectations, access reviews for cleanup, and staying current through ongoing, continuous learning. Only through these three pillars, organizations can sustain governance despite changing teams, requirements and features.
👉 What are the authority levels in SharePoint? Authority levels refer to the permission levels that have already been mentioned. They define the scope of control that a user has in the SharePoint environment.
Configuring Permissions in SharePoint
Below, we will explore the practical application of different access rules within SharePoint, such as read, write, edit, and delete, and how they can be tailored to suit various business scenarios. We’ll then explain the modern features of SharePoint that simplify the permission-setting process, illustrating with key examples how leveraging these tools can improve the management of access rights and benefit overall organizational workflow.
Applying access rules in practice: permissions to read, write, edit, etc.
We’ve already covered access rules in SharePoint control, but it’s worth reiterating those along with their practical use cases:
- Read: Users can view content but cannot make any changes. Apply this to employees who need to reference material but not alter it, such as viewing company policies.
- Write: Typically combined with read access, users can add new content. For example, team members uploading documents to a project site.
- Edit: Allows users to both add and alter existing content. This is useful for collaborative workspaces where team members need to modify documents or list items.
- Delete: Users can remove content. This should be limited, possibly restricted to project leads who can delete outdated files from a collaborative workspace.
- Full Control: Grants all permission types including managing permissions and site settings. This should be exclusive to site collection administrators.
Here are a few more specific use cases:
- HR document libraries: Read access could be granted broadly, whereas edit access might be limited to HR team members only, ensuring sensitive data is not altered by unauthorized users.
- Financial reports: Financial teams may have edit or full control permissions, but other departments might only have read access to ensure data integrity.
The impact of applying these rules correctly ensures that sensitive data is protected, and that collaboration is facilitated without compromising data security.
Using modern SharePoint features to simplify permission settings
Modern SharePoint brings several enhanced features that make the process of setting permissions more convenient:
- SharePoint groups: Instead of setting permissions for individuals, grouping users simplifies assigning the same permission level to many users at once.
- Permission levels: These are preset groups of permissions designed to make it easy to assign roles. For instance, SharePoint “Contribute” permissions include permissions to add, edit, and delete items.
- Inheritance: Subsites, lists, and libraries inherit permissions from their parent by default, making it easier to manage permissions across related resources.
- Sharing links: For external users or temporary access needs, sharing links with specific permissions can limit access and auto-expire.
- Microsoft 365 groups integration: When you create a new site, it’s associated with an Microsoft 365 group, synchronizing group membership across services.
- Break inheritance button: Easily customize permissions for a particular resource directly from the UI, without having to delve into complex settings.
- Limited access user permission lockdown mode: This feature helps secure restricted content from users with limited access.
Examples:
- Project sites: Use Microsoft 365 Groups to manage a project site. When new team members are added to the group, they’ll automatically get the necessary permissions in SharePoint.
- Confidential documents: Use secured links for external consultants to access specific documents without exposing other content.
These features, coupled with a robust governance plan, can dramatically reduce the complexity of permissions management and help ensure that users have the right level of access.
How do I manage user permissions in SharePoint: Managing permissions common tasks
Managing permissions in SharePoint involves several tasks that administrators commonly need to carry out to ensure proper access control and security. Below are the basic steps for each of those common tasks—in a tabular format for easy reference—assuming you’re using a modern SharePoint Online environment:
| View permissions in SharePoint | To view who has permissions to a particular site, list, library, folder or item: Navigate to the item, then click on “Settings” and select the appropriate settings option.Click on “Site permissions” or “Permissions for this document library”/”Permissions for this list”.Here you will see a list of groups and individuals with access, along with their assigned permission levels. |
| Edit permissions in SharePoint | To edit permissions for a site, list, library, folder, or item: Navigate to the SharePoint item you want to manage.Click on “Settings” then “Site settings” or “Library settings”/”List settings”.Click on “Site permissions” or “Permissions for this document library”/”Permissions for this list”.Select the checkbox next to the group or individual you want to edit permissions for, then click “Edit User Permissions”.Change the permissions as needed and click “OK” to save the changes. |
| Change permissions in SharePoint | This process is very similar to editing permissions. You need to first go to the site, list, or library permissions and edit them as needed, assigning or removing groups or individuals to different permission levels. |
| Audit SharePoint permissions | To audit permissions, you typically need to generate reports to determine who has access to what. You can do this: Using PowerShell scripts to create custom reports.Using third-party tools that provide detailed permissions reporting.Checking individual items for permission levels if you do not have a large site. |
| Stop inheriting permissions in SharePoint | To stop a site, list, or library from inheriting permissions: Navigate to the item, click on “Settings,” and go to the appropriate settings page.Click on “Permissions for this document library”, “Permissions for this list” or “Site permissions”.Click “Stop Inheriting Permissions”.Confirm the action, and set up unique permissions as required. |
| How do I allow access to my SharePoint site? | To allow access to your SharePoint site: Navigate to your site Open permissions settings by clicking on ‘Site Permissions’ under the ‘Site settings.’Use the ‘Invite people’ option to add users or groups by entering email addresses or names. Then, assign the appropriate permission level.Use the ‘Share’ option (often found at the top of the site) to send an invitation to new users to access the site with the designated permissions. |
| Grant permissions in SharePoint | To grant permissions to a user or group: Go to the site, list, or library where you want to change permissions.Click on “Settings” and select either “Site settings” or “Library settings”/”List settings”.Click “Site permissions” or “Permissions for this document library”/”Permissions for this list”.Click “Grant Permissions”.Enter the user’s name or email address, or select a SharePoint group.Choose the permission level (such as Contribute, Read, Edit), then click “Share” or “OK”. |
| Delete unique permissions in SharePoint | To remove unique permissions and revert to inheriting permissions from the parent site, list, or library: Navigate to the site, library, or list you want to manage.Click on “Settings”, then select “Site settings” or “Library settings”/”List settings”.Under “Permissions and Management,” click on “Permissions for this document library” or “Permissions for this list”.On the permissions page, click “Manage Parent” if the item is inheriting permissions or “Delete unique permissions” for items with unique permissions, and confirm the action. |
SharePoint Permissions Best Practices: Managing Permissions in SharePoint
Effective SharePoint governance demands balancing intuitive access with security and compliance through tailored permission strategies including:

- Planning before implementing: Before you set up permissions, create a clear plan that outlines the various roles within your organization and the corresponding access levels they require. This reduces the complexity of permission management.
- Following the principle of least privilege: Assign users the minimum level of access they need to perform their duties. Avoid over-privileged accounts which increase the risk of security breaches.
- Using SharePoint groups: Whenever possible, assign permissions to groups rather than direct to individual users. This streamlines management and ensures consistent permissions across users with similar roles.
- Regular auditing and reviewing: Regularly monitoring who has access to what information is essential. Schedule permission reviews to remove or adjust access as roles within the organization change.
- Training: Training users on the implications of permissions and data sharing within SharePoint is crucial. They should understand best practices and the importance of maintaining the integrity of the data they’re working with.
- Limiting unique permissions: Try to avoid breaking inheritance and creating unique permissions unless necessary. Unique permissions can make the system complex and difficult to manage over time.
- Leveraging inheritance: Utilize the permissions inheritance feature for subsites, lists, and libraries whenever appropriate to manage permissions more effectively.
- Implementing governance policies: Develop and enforce governance policies concerning the management of permissions and user access throughout the organization.
- Using advanced security settings: For sensitive information, consider using advanced security settings like document encryption, security labels, and IRM policies.
👉 What is a SharePoint permissions management tool? A SharePoint permissions tool is a software solution designed to simplify, streamline, and enhance the management of user permissions within SharePoint. Since SharePoint’s native permission settings can sometimes be complex and difficult to manage, especially within large organizations or in environments with intricate access control requirements, these tools provide invaluable support. Among the variety of SharePoint permissions management tools, you might encounter platforms, such as ShareGate, AvePoint, and SolarWinds, each offering a mix of powerful functionalities. If you’re looking for a SharePoint Online permissions management tool free, you’d generally look towards community tools, open-source projects, or leveraging the native capabilities of SharePoint Online and the associated PowerShell cmdlets.
How to avoid common mistakes when setting permissions
Even experienced SharePoint administrators can fall prey to common permissions-related pitfalls. Here’s how to avoid them:
- Overly complex permissions: Avoid creating an intricate web of permissions that are difficult to track and manage. Simplify by utilizing groups and maintaining clear documentation of permissions settings.
- Neglecting to remove old accounts: Always remove access for users who have left the organization or moved to different roles that do not require the same level of access.
- Ignoring permission inheritance: Breaking inheritance without understanding it can result in SharePoint permissions levels that are confusing and inconsistent. Ensure there’s a valid reason for breaking inheritance.
- Lack of auditing: Not regularly auditing who has access to what can lead to permission creep, where individuals accumulate access rights over time, exceeding what is needed for their job.
- Forgetting to train users: Failure to educate users on how to use and share SharePoint content can lead to accidental oversharing of sensitive information.
- Failure to use limited access: Not using or misunderstanding the ‘Limited Access’ permission, which enables a user to browse to an item or a document without giving full read access to the parent site.
- Direct permissions to individuals: Directly granting permissions to individuals, rather than through group membership, can make for a permissions management nightmare as the number of users grows.
To resolve problems arising from incorrect permission configurations, conduct a thorough audit of the current permissions setup, re-plan the permissions architecture using best practices, and reassign permissions appropriately. It may be time-consuming initially, but it will result in a more secure and manageable SharePoint environment.
Guidelines for Creating the SharePoint Permissions Report
Effective management and control of permissions are at the heart of securing and maintaining regulatory compliance within SharePoint environments. To achieve this, administrators must be equipped with the right tools and techniques for meticulous analysis and continuous monitoring of permission settings.
In the subsequent sections, we will outline the primary tools available within SharePoint for analyzing and monitoring permissions, describe additional external applications that can enhance this process, and provide practical guidance on creating and interpreting SharePoint user permissions reports.
Tools and techniques for analyzing and monitoring permissions in SharePoint
Monitoring permission configurations ensures sustained governance. SharePoint and third-party tools enable insight through:
Built-in SharePoint tools:
- Permissions report in SharePoint admin center: SharePoint Admin Center provides reports that let you see permissions set across sites.
- SharePoint audit log reports: The audit log reports can be configured to track actions on sites, content types, lists, libraries, list items, and library files within your SharePoint site collection.
- Site collection administrators: Assigning site collection administrators is itself a tool as they have the overview of all site activities including permissions.
PowerShell Cmdlets: PowerShell can be used to create custom scripts that generate detailed permission reports, especially useful in on-premises environments where administrators require more granular control.
External tools and applications: Many third-party tools offer extensive permissions reporting features, including automated reports, alerts on unusual activities, and audit trails. Examples include:
- ShareGate
- Metalogix
- AvePoint
These external tools often provide more user-friendly interfaces and extra functionalities, such as identifying nested groups, comparing permissions between different times, or highlighting permissions changes.
How to create and interpret permission reports for security and compliance
Creating and interpreting permission reports is not just a periodic compliance task, but a crucial continuous practice that forms the backbone of data security and access management. This section highlights the essential steps for generating comprehensive SharePoint online permissions reports and provides insights into how to analyze them for actionable intelligence.
Creating permission reports
Reports are indispensable tools for auditing access controls and asserting compliance with internal and external regulatory standards.
Here are the basic steps you need to follow to generate an appropropriate permission report:
- Determine the scope: Decide whether the reports should cover an entire site collection, a single site, or specific lists and libraries.
- Choose the right tool: For most needs, the SharePoint Admin Center is sufficient. For deeper analysis, a third-party tool might be necessary.
- Configure audit log settings: If using SharePoint audit logs, configure them to report on the types of changes or events that are relevant to your security concerns.
- Generate the report: In SharePoint, you can run reports directly from the UI. With PowerShell or third-party tools, follow the application’s documentation for report generation.
Interpreting the reports
Simply generating reports is not sufficient; it is the analysis and understanding of their contents that allow administrators to act on insights, address vulnerabilities, and enforce proper data governance protocols.
Here’s how to interpret reports and discern patterns indicating improper access:
- Identify excessive permissions: Look for users who have more permissions than necessary for their role.
- Spot inheritance breaks: Find locations where permission inheritance is broken, as this may be an area of increased risk.
- Review external sharing settings: Monitor where and what content is shared with external users.
- Audit group membership changes: Observe changes in group memberships which can affect a wide range of permissions.
Important metrics and KPIs
Key metrics and performance indicators (KPIs) serve as the quantifiable measures that inform you whether your permissions strategy aligns with your security and compliance objectives or if there are gaps that need attention. Below are a few suggestions to look out for:
- Number of users with full control: Should be minimal and closely monitored.
- Number of unique permissions: The higher this number, the more complex—and potentially insecure—your environment.
- Permissions changes over time: Increases in permissions levels could indicate a breach or internal misuse.
- Orphaned users: Accounts that still have permissions but are no longer with the company can be a severe security risk.
Permission reports only prove as valuable as an organization’s responsiveness to the intelligence uncovered. By cross-referencing audit logs with established governance policies and compliance needs, administrators can pinpoint gaps, remediate access, and ultimately refine their strategy. In this way, routine permission auditing moves from obligation to opportunity. Reports feed continuous refinement of access alignments amid changing collaboration dynamics, sustaining security not through initial conditions alone but ongoing vigilance.
Managing SharePoint Permissions When Installing Web Parts and Apps
Web parts and applications are transformative elements within SharePoint Online (and SharePoint On-Premises), providing vital extensions that greatly enhance the platform’s functionality. Whether sourced from the SharePoint Store or custom-built, these components can add sophisticated features, streamline workflows, and offer tailored user experiences. An integral aspect of their integration is their interaction with the existing SharePoint permissions model to ensure both the expanded functionality and organizational data are securely managed.
It’s essential for administrators to consider how these third-party components interface with SharePoint permissions:
Web parts and application interaction with SharePoint permissions:
- Permission management: Web parts and applications are typically engineered to honor established SharePoint permissions. For instance, they may display content conditionally, based on whether a user has the requisite permissions. A pertinent example is the Virto Calendar—a web part that enhances the visibility of calendars while respecting item-level permissions.
- Permission-aware functionality: Applications may augment the SharePoint interface with additional actions—like editing or deleting—but these actions inherit user-specific permissions to enforce security and governance policies.
- Managing permissions: Certain applications may empower administrators to manage SharePoint permissions directly, thereby streamlining the access control process, from tweaking user privileges to auditing.
- SharePoint API integration: Leveraging SharePoint APIs (REST API, JSOM) allows for dynamic and sophisticated control over permissions. Custom development can harness these APIs to cater to complex scenarios beyond what is possible with out-of-the-box features.
- Setting custom permissions: Some applications could offer bespoke permission configurations, providing fine-tuned control over who can access and interact with the application, separate from SharePoint’s default permission hierarchy.
- Auditing and reporting: Enhanced auditing features in applications can help monitor permission alterations, provide insights into security weaknesses, and aid in maintaining compliance with organizational or regulatory mandates.
Virto Calendar and SharePoint calendar permissions
Let’s illustrate how permissions operate with web parts by examining the Virto Calendar web part as a case in point.
Working with permissions in Virto Calendar is a multi-layered process that involves understanding and setting permissions at different levels to ensure proper access control and functionality within the Virto Calendar environment:
First level: SharePoint permissions settings
At the foundational level, permissions are set within SharePoint itself. Each SharePoint list and event list comes with its own “Permissions for this list” settings, which by default, inherit from the permissions of the site it resides on. These permissions can be viewed and modified by navigating to the “Permissions Levels” menu on the site’s header.
Pic. 10. Creating user groups and adding permissions in the “Permission Levels”.
Here, administrators have the capability to create user groups with varied permissions, ranging from view-only access to full control. These settings directly influence how Virto Calendar functions, as it inherits permissions from these SharePoint lists.
Second level: Virto Calendar permissions settings
The second level pertains specifically to Virto Calendar permissions. Access to these settings can be found by clicking the cog icon and selecting “Settings,” followed by the “Permission” tab.
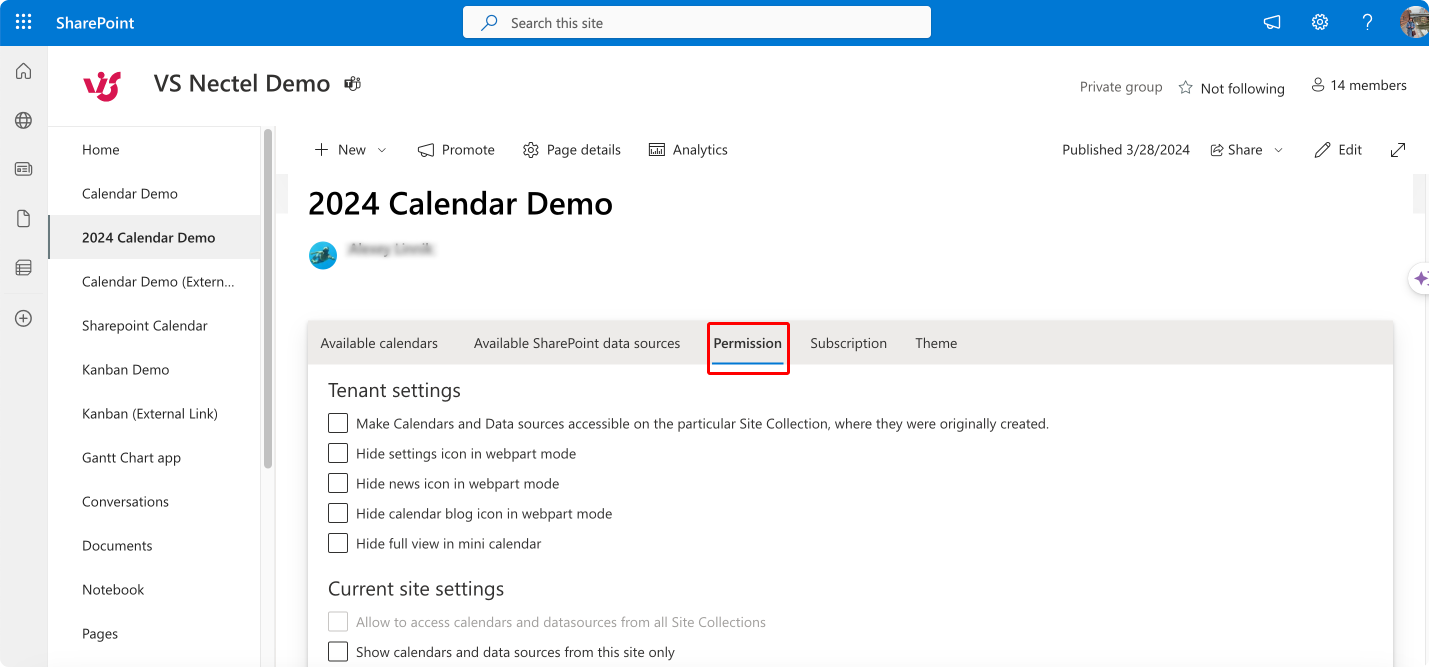
Pic. 11. Reviewing and editing permissions in the “Permissions” tab in the Virto Calendar settings.
Within this interface, you can set permissions for the tenant, the current site, or individual users. This includes deciding if you want to make a calendar and its data sources accessible only within the site collection they were created, or if you want to show calendars and sources from this site only. Additionally, you can assign roles such as calendar manager or license manager to users by typing in their names or email addresses. It’s important to note that site collection administrators have inherent permissions that cannot be altered here; changes to these administrators must be done through the site collection settings.
User permissions
Virto Calendar offers specific roles and permissions. The permissions at the SharePoint site level are set by the site administrator, and Virto Calendar inherits these permissions. Moreover, within the Virto Calendar permissions, users can be assigned as calendar managers, empowering them to modify calendar settings.
For efficient project management, it’s essential to integrate these permission levels effectively. SharePoint Permissions Settings form the base of access control, determining what users can see and do within SharePoint lists. These permissions then extend to how Virto Calendar operates, with additional customization available in the Overlay’s specific settings to fine-tune user roles and access within the calendar environment.
Strategies for permission management
- Synchronize SharePoint and Virto Calendar permissions: Ensure that permissions set in SharePoint are reflected appropriately in Virto Calendar to maintain consistency.
- Assign appropriate roles: Use the Virto Calendar permission settings to assign calendar managers and license managers, tailoring access and control to the needs of your project.
- Manage site collection administrators: Regularly review and update the list of site collection administrators to align with current project requirements and team structures.
By understanding and managing these permission levels, Virto Calendar users can maintain a secure and well-organized calendar system, ensuring that the right individuals have the appropriate levels of access to perform their roles effectively within the project management process. You can read more on permissions in the Virto Calendar here: User Permissions
Conclusion
The careful and strategic management of permissions in SharePoint is essential for the optimal and secure operation of this powerful collaboration platform. Throughout this article, we have emphasized the importance of establishing a robust permissions infrastructure that streamlines who has access to what resources within your organization. It’s critical that these practices are not only implemented but maintained regularly to ensure ongoing security and efficiency.
To stay on top of your SharePoint permissions management, we highly recommend referencing the official Microsoft documentation. It is an invaluable resource for staying informed about the latest best practices, updates, and tools designed to help you manage permissions accurately and effectively:
Additionally, it’s worth highlighting that applications from VirtoSoftware are developed with a keen understanding of SharePoint’s permission model, ensuring that they work seamlessly within your existing security framework. By strictly following your security policies, VirtoSoftware applications help maintain the integrity of your data without sacrificing functionality.
For those interested in enhancing their SharePoint experience while preserving security and compliance, we encourage exploring our offerings further. Our applications are crafted to provide additional layers of functionality without compromising on the commitment to permissions integrity and security compliance within SharePoint. For more information on VirtoSoftware’s solutions, please visit the following pages:
- VirtoSoftware’s SharePoint Online Apps
- VirtoSoftware’s SharePoint On-Premise Web Parts
- User Permission in Virto Calendar App
Additionally, you may want to explore the following pages on our blog to learn more about SharePoint governance, the security and limitations of other apps within Microsoft environment:
- Microsoft Teams Limitations
- MS Team Security Guide
- SharePoint Online vs SharePoint on Premise
- SharePoint Calendar Permissions
References:
(1) SharePoint stats from Gitnux.





